2014 Latest Pass4sure&Lead2pass Juniper JN0-314 Exam Questions
Vendor: Juniper
Exam Code: JN0-314
Exam Name: Junos Pulse Access Control, Specialist (JNCIS-AC)
QUESTION 1
On a MAG Series device, where is the preauthentication sign-in message configured?
A. On the configuration page for the sign-in notification message
B. On the wireless user realm authentication policy
C. On the sign-in policy of the URL being used by the wireless users
D. On the sign-in page of the URL being used by the wireless users
Answer: C
QUESTION 2
Click the Exhibit button. A user logs in, is assigned the default role, and successfully loads the Host Enforcer policies shown in the exhibit.
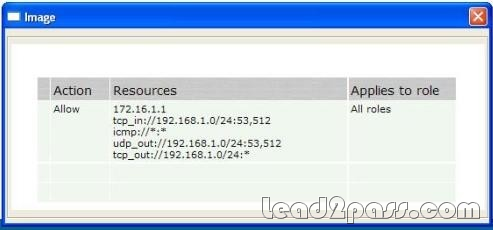
Which three statements are true? (Choose three.)
A. The local host will respond to ICMP echo-request packets from 192.168.53.10.
B. The local host will respond to UDP port 53 requests from 192.168.1.25.
C. The local host can send any packet of any type to host 172.16.1.1.
D. The local host will accept any packet of any type from host 172.16.1.1.
E. The local host can send packets to UDP port512 on server 192.168.53.10.
Answer: ACD
QUESTION 3
Which two actions are available in the GUI for creating location awareness rules? (Choose two.)
A. WINS server
B. DNS server
C. IP reachability
D. Resolve address
Answer: BD
QUESTION 4
You are the network administrator for your company. A user is complaining that they are not able to access the network with the Junos Pulse client. You run a packet capture on the network interface to monitor the 802.1X authentication process. You notice that after the EAP- request/identity packet is received, and the supplicant responds with an EAP-response/identity packet, no further communication occurs for several seconds.
What are three causes for this behavior? (Choose three.)
A. The authenticator is not licensed to support Junos Pulse.
B. The authenticator did not receive the EAP-response/identity packet.
C. The authentication server is not receiving the RADIUS packet containing the EAP- response/identity data.
D. The authenticator is sending the request over its loopback interface.
E. The authentication server is sending back a RADIUS response packet, but the authenticator is not forwarding
the response back to the supplicant.
Answer: BCE
QUESTION 5
An administrator has created three different Odyssey Access Client preconfiguration files and assigned them to three different roles in the same realm.
Which action should the administrator take to ensure that users get the correct Odyssey Access Client preconfiguration file?
A. Configure each user account in the auth server with the appropriate Odyssey Access Client preconfiguration
files.
B. Configure the role-mapping rules with the appropriate Odyssey Access Client preconfiguration files.
C. Ensure that merge roles is selected in the role-mapping rules.
D. Ensure that the first role a user is mapped to is the role with the appropriate Odyssey Access Client
preconfiguration file.
Answer: D
QUESTION 6
You want to create a Host Checker policy that looks for a specific antivirus product that is running on your client machines, but the predefined antivirus options do not include the antivirus product version that you use.
Which feature should you verify the antivirus product is up to date?
A. Enhanced Endpoint Security
B. DP signatures
C. Antivirus licensing
D. Endpoint Security Assessment Plug-in
Answer: D
QUESTION 7
What are three benefits of IF-MAP Federation? (Choose three.)
A. Enables seamless access for remote access users to firewall enforcer protected resources.
B. Scales a Junos Pulse Access Control Service deployment beyond the capacity of a single cluster.
C. Enables dynamic configuration synchronization across multiple MAG Series devices.
D. Provides a substitute for WAN clustering among geographically separated MAG Series devices.
E. Shares non-localized DP integration and IPsec configuration information between multiple Junos Pulse
Access Control Service instances.
Answer: ABE
QUESTION 8
Which three authentication server types are supported for retrieving user attributes used in role- mapping rules? (Choose three.)
A. LDAP
B. S/Key
C. TACACS+
D. RADIUS
E. SiteMinder
Answer: ADE
QUESTION 9
You have an SRX Series Layer 2 enforcer providing 802.1X authentication for connected endpoints. Your security policy requires that users who fail their authentication be placed in a specific VLAN.
On the Layer 2 enforcer, at the [edit protocols dot1x authenticator interface] hierarchy for each participating interface, what provides this functionality?
A. guest-vlan
B. auth-fail-vlan
C. server-reject-vlan
D. server-fail-vlan
Answer: C
QUESTION 10
A company has completed two acquisitions over the previous year. Each of the acquired companies was allowed to keep its own independent authentication server. The network administrator has been asked to roll out the Junos Pulse Access Control Service to users within the original company along with each of the two acquired organizations. The administrator configures three authentication realms, one for each independent authentication server, and associates them all with a single sign-in policy. All of the client endpoints are running Junos Pulse on their Windows XP desktops.
When a user signs in to the Junos Pulse Access Control Service, which statement is correct?
A. The first authentication realm that was added to the sign-in policy is used by default.
B. The user is allowed to choose the correct authentication realm from a list presented by Junos Pulse.
C. When Junos Pulse is initially installed on the desktop, it must be configured with the correct realm.
D. This is not an allowed configuration; the administrator should configure separate sign-in policies for
each realm.
Answer: B
QUESTION 11
You want to customize access to the corporate network so that agentiess users are instructed to obtain a certificate before accessing the network.
Which two configurations solve this problem? (Choose two.)
A. Create a custom sign-in page with specific instructions in the "Instructions" field.
B. Create a custom sign-in page with specific "Missing Certificate" messages in the "Custom error messages"
field.
C. Create a custom sign-in policy with specific instructions in the "Instructions" field.
D. Create a custom sign-in notification and assign it to the "Pre-Auth Sign-in Notification" in the sign-in policy.
Answer: AD
QUESTION 12
You want to restrict access to a role based on the client machine from which the user is accessing the network.
Which two role restrictions accomplish this goal? (Choose two.)
A. user name
B. password length
C. certificate
D. Host Checker
Answer: CD
QUESTION 13
You are configuring an LDAP authentication server, and you want to configure role-mapping rules based on group membership. When you attempt to search for groups in the server catalog, no groups appear.
Assuming the LDAP server is reachable and functioning properly, in the admin GUI. Which two parts of the configuration should you verify are correct? (Choose two.)
A. Finding user entries
B. Authentication required?
C. LDAP Server Type
D. Determining group membership
Answer: BD
If you want to pass Juniper JN0-314 successfully, donot missing to read latest lead2pass Juniper JN0-314 practice tests.
If you can master all lead2pass questions you will able to pass 100% guaranteed.