100% Valid 70-410 445q Exam Practice Questions From Lead2pass To Pass Exam Easily (121-140)
Attention Please:Latest new version 70-410 exam dumps can now free download on Lead2pass.com, all questions are updated timely by our experts covering all aspects. After have a train on our 70-410 445q brain dumps, you will pass the exam quickly.
QUESTION 121
You have a server named Server1 that runs Windows Server 2012 R2.
Server1 has following storage spaces:
– Data
– Users
– Backups
– Primordial
You add an additional hard disk to Server1.
You need to identify which storage space contains the new hard disk.
Which storage space contains the new disk?
A. Data
B. Primordial
C. Users
D. Backups
Answer: B
Explanation:
New Disks (Unallocated space) added to Primordial spacePrimordial Pool?
All storage that meets acceptable criteria for Storage Spaces will be placed in the Primordial Pool. Thiscan be considered the default pool for devices from which any other pools will be created. Notice that there are no other virtual disks or pools at this point. The Primordial Pool will only consist ofphysical storage devices that do not belong to any other pools.
http://blogs.technet.com/b/canitpro/archive/2012/12/13/storage-pools-dive-right-in.aspx
http://blogs.technet.com/b/askpfeplat/archive/2012/10/10/windows-server-2012-storagespaces-is-it-for-youcould-be.aspx
QUESTION 122
You have a server named Server1. Server1 runs Windows Server 2012 R2 and has the File and Storage Services server role installed.
You attach four 500-GB disks to Server1.
You need to configure the storage to meet the following requirements:
– Storage for an application named Application1 must be provided. Application1 requires 20 GB and will require a maximum of 800 GB in three years.
– Storage for an application named Application2 must be provided. Application2 requires 20 GB and will require a maximum of 900 GB in three years.
– The solution must provide the ability to dynamically add storage without requiring configuration changes to the applications.
– The storage must be available if a single disk fails.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. From File and Storage Services, create virtual disks by using fixed provisioning.
B. From File and Storage Services, create a storage pool that uses all four disks.
C. From Disk Management, create two new mirror volumes that use two disks each.
D. From Disk Management, create a new RAID-5 volume that uses all four disks.
E. From File and Storage Services, create virtual disks by using thin provisioning.
Answer: BE
Explanation:
Original answer is AB.
But the correct answer is B and E. it can’t be A, because a fixed disk can’t get expanding.
QUESTION 123
Your network contains multiple subnets.
On one of the subnets, you deploy a server named Server1 that runs Windows Server 2012 R2.
You install the DNS Server server role on Server1, and then you create a standard primary zone named contoso.com.
You need to ensure that client computers can resolve single-label names to IP addresses.
What should you do first?
A. Create a reverse lookup zone.
B. Convert the contoso.com zone to an Active Directory-integrated zone.
C. Configure dynamic updates for contoso.com.
D. Create a GlobalNames zone.
Answer: D
Explanation:
D. use GlobalNames zones in Windows Server 2008 to take advantage of single-label names Providing Single-Label DNS Name Resolution:
While Domain Name System (DNS) is the predominant name-resolution technology in TCP/IP networks, Windows Internet Name Service (WINS) is deployed in many networks as an alternative name-resolution protocol.
GlobalNames Zone (GNZ) feature: The GNZ feature is designed to enable DNS resolution of these single-label, static, global names. You can deploy a GNZ in a single forest or across multiple forests.
GNZ is intended to aid the retirement of WINS. It is not a replacement for WINS. GNZ is not intended to support the single-label name resolution of records that are registered dynamically and therefore not managed by IT administrators. GNZ does make it possible for you to provide single-label name resolution of a fixed set of host computers whose names are guaranteed to be both global and unique.
http://technet.microsoft.com/en-us/library/cc731744.aspx
http://technet.microsoft.com/en-us/library/cc816610(v=ws.10).aspx
QUESTION 124
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has six network adapters. Two of the network adapters are connected to a network named LAN1, two of the network adapters are connected to a network named LAN2, and two of the network adapters are connected to a network named LAN3.
You create a network adapter team named Team1 from the two adapters connected to LAN1.
You create a network adapter team named Team2 from the two adapters connected to LAN2.
A company policy states that all server IP addresses must be assigned by using a reserved address in DHCP.
You need to identify how many DHCP reservations you must create for Server1.
How many reservations should you identify?
A. 3
B. 4
C. 6
D. 8
Answer: B
Explanation:
2 Adapters = LAN1 = Team1 = 1 IP
2 Adapters = LAN2 = Team2 = 1 IP
2 Adapters = LAN3 = No Team = 2 IP
1 + 1 + 2 = 4
QUESTION 125
Your network contains an Active Directory domain named contoso.com.
All servers run Windows Server 2012 R2. The domain contains a server named Server1.
You open Review Options in the Active Directory Domain Services Configuration Wizard, and then you click View script.
You need to ensure that you can use the script to promote Server1 to a domain controller.
Which file extension should you use to save the script?
A. .pal
B. .bat
C. .xml
D. .cmd
Answer: A
QUESTION 126
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server!. Server1 runs a Server Core installation of Windows Server 2012 R2.
You install the DNS Server server role on Server1.
You need to perform the following configurations on Server1:
– Create an Active Directory-integrated zone named adatum.com.
– Send unresolved DNS client queries for other domain suffixes to the DNS server of your company’s Internet Service Provider (ISP).
Which Windows PowerShell cmdlets should you use? To answer, drag the appropriate cmdlet to the correct configuration in the answer area. Each cmdlet may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. 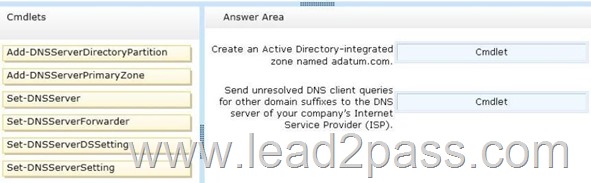
Answer: 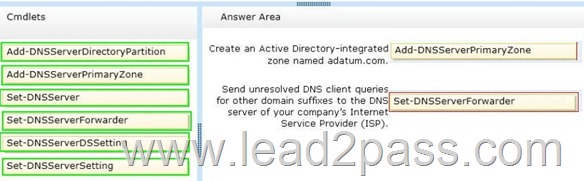
Explanation:
Add-DnsServerDirectoryPartition: Creates a DNS application directory partition.
Add-DnsServerPrimaryZone: Adds a primary zone to a DNS server.
Set-DNSServer Overwrites a DNS server configuration.
SET-DNSServerForwarder Changes forwarder settings on a DNS server Set-DNSServerDSSetting Modifies DNS Active Directory settings.
Set-DNSServerSetting Modifies DNS server settings.
http://technet.microsoft.com/en-us/library/jj649942(v=wps.620).aspx
http://technet.microsoft.com/en-us/library/jj649876(v=wps.620).aspx
http://technet.microsoft.com/en-us/library/jj649845(v=wps.620).aspx
http://technet.microsoft.com/en-us/library/jj649887(v=wps.620).aspx
http://technet.microsoft.com/en-us/library/jj649874.aspx
http://technet.microsoft.com/en-us/library/jj649909.aspx
QUESTION 127
Your network contains an Active Directory domain named contoso.com. The network contains 500 client computers that run Windows 8.
All of the client computers connect to the Internet by using a web proxy.
You deploy a server named Server1 that runs Windows Server 2012 R2.
Server1 has the DNS Server server role installed.
You configure all of the client computers to use Server1 as their primary DNS server.
You need to prevent Server1 from attempting to resolve Internet host names for the client computers.
What should you do on Server1?
A. Create a primary zone named ".".
B. Configure the Security settings of the contoso.com zone.
C. Create a zone delegation for GlobalNames.contoso.com.
D. Create a stub zone named "root".
Answer: A
Explanation:
When you install DNS on a Windows server that does not have a connection to the Internet, the zone for the domain is created and a root zone, also known as a dot zone, is also created.
This root zone may prevent access to the Internet for DNS and for clients of the DNS. If there is a root zone, there are no other zones other than those that are listed with DNS, and you cannot configure forwarders or root hint servers.
Root domain
This is the top of the tree, representing an unnamed level; it is sometimes shown as two empty quotation marks (""), indicating a null value. When used in a DNS domain name, it is stated by a trailing period (.) to designate that the name is located at the root or highest level of the domain hierarchy. In this instance, the DNS domain name is considered to be complete and points to an exact location in the tree of names. Names stated this way are called fully qualified domain names (FQDNs).
DNS Domain Name Hierarchy:
QUESTION 128
Your network contains an Active Directory domain named contoso.com.
The domain contains 100 user accounts that reside in an organizational unit (OU) named 0U1.
You need to ensure that a user named User1 can link and unlink Group Policy objects (GPOs) to OU1. The solution must minimize the number of permissions assigned to User1.
What should you do?
A. Modify the permissions on OU1.
B. Run the Set-GPPermission cmdlet.
C. Add User1 to the Group Policy Creator Owners group.
D. Modify the permissions on the User1 account.
Answer: A
Explanation:
http://www.howtogeek.com/50166/using-the-delegation-of-control-wizard-to-assign-permissions-in-server-2008/
QUESTION 129
You have a server that runs Windows Server 2012 R2.
The server contains the disks configured as shown in the following table. 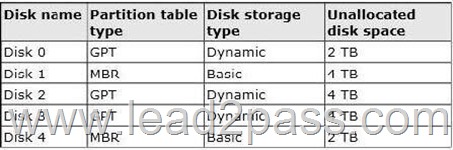
You need to create a volume that can store up to 3 TB of user files.
The solution must ensure that the user files are available if one of the disks in the volume fails.
What should you create?
A. a mirrored volume on Disk 1 and Disk 4
B. a mirrored volume on Disk 2 and Disk 3
C. a RAID-5 volume on Disk 1, Disk 2, and Disk 3
D. a spanned volume on Disk 0 and Disk 4
Answer: B
Explanation:
A mirrored volume provides an identical twin of the selected volume. All data written to the mirrored volume is written to both volumes, which results in disk capacity of only 50 percent. Any volume can be mirrored, including the system and boot volumes. The disk that you select for the shadow volume does not need to be identical to the original disk in size, or in its number of tracks and cylinders. This means that you do not have to replace a failed disk with an identical model. The unused area that you select for the shadow volume cannot be smaller than the original volume. If the area that you select for the shadow volume is larger than the original, the extra space on the shadow disk can be configured as another volume.
Dynamic disks provide features that basic disks do not, such as the ability to create volumes that span multiple disks (spanned and striped volumes) and the ability to create fault-tolerant volumes (mirrored and RAID-5 volumes).
The following operations can be performed only on dynamic disks:
Create and delete simple, spanned, striped, mirrored, and RAID-5 volumes. Extend a simple or spanned volume. Remove a mirror from a mirrored volume or break the mirrored volume into two volumes. Repair mirrored or RAID-5 volumes. Reactivate a missing or offline disk.
You need at least two dynamic disks to create a mirrored volume.
Mirrored volumes are fault tolerant and use RAID-1, which provides redundancy by creating two identical copies of a volume.
Mirrored volumes cannot be extended.
Both copies (mirrors) of the mirrored volume share the same drive letter.
http://technet.microsoft.com/en-us/library/cc779765%28v=ws.10%29.aspx
http://msdn.microsoft.com/en-us/library/windows/desktop/aa363785%28v=vs.85%29.aspx
http://technet.microsoft.com/en-us/library/cc938487.aspx
QUESTION 130
What should you do for server core so it can be managed from another server 2012 R2?
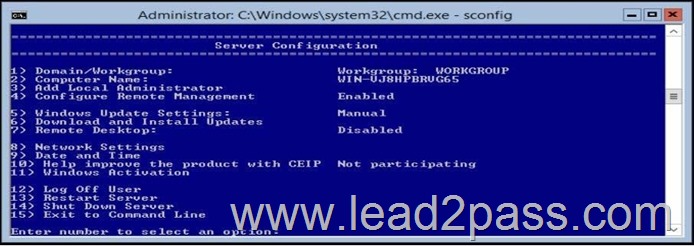
A. 1
B. 2
C. 3
D. 4
E. 5
F. 6
G. 7
H. 8
I. 9
J. 10
K. 11
L. 12
M. 13
N. 14
O. 15
Answer: H
Explanation:
4) Configure Remote Management is already "Enabled". 8)
Network Settings
You can configure the IP address to be assigned automatically by a DHCP Server or you can assign a static IP address manually. This option allows you to configure DNS Server settings for the server as well.
http://technet.microsoft.com/en-us/library/jj647766.aspx
QUESTION 131
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1.
Server1 runs Windows Server 2012 R2. On Server1, you create a printer named Printer1.
You share Printer1 and publish Printer1 in Active Directory.
You need to provide a group named Group1 with the ability to manage Printer1.
What should you do?
A. From Print Management, configure the Sharing settings of Printer1.
B. From Active Directory Users and Computers, configure the Security settings of Server1-Printer1.
C. From Print Management, configure the Security settings of Printer1.
D. From Print Management, configure the Advanced settings of Printer1.
Answer: C
Explanation:
Set permissions for print servers
Note:
Open Print Management.
In the left pane, clickPrint Servers, right-click the App1icable print server and then clickProperties. On theSecuritytab, underGroup or users names, click a user or group for which you want to set permissions.
UnderPermissions for <user or group name>, select theAlloworDenycheck boxes for the
permissions listed as needed.
To editSpecial permissions, clickAdvanced.
On thePermissionstab, click a user group, and then clickEdit. In thePermission Entrydialog box, select theAlloworDenycheck boxes for the permissions that you want to edit.
Reference: Set Permissions for Print Servers
QUESTION 132
Your network contains an Active Directory domain named contoso.com.
All servers run Windows Server 2012 R2.
Client computers run either Windows 7 or Windows 8.
All of the computer accounts of the client computers reside in an organizational unit (OU) named Clients. A Group Policy object (GPO) named GP01 is linked to the Clients OU. All of the client computers use a DNS server named Server1.
You configure a server named Server2 as an ISATAP router.
You add a host (A) record for ISATAP to the contoso.com DNS zone.
You need to ensure that the client computers locate the ISATAP router.
What should you do?
A. Run the Add-DnsServerResourceRecord cmdlet on Server1.
B. Configure the DNS Client Group Policy setting of GPO1.
C. Configure the Network Options Group Policy preference of GPO1.
D. Run the Set-DnsServerGlobalQueryBlockList cmdlet on Server1.
Answer: D
Explanation:
Windows Server 2008 introduced a new feature, called "Global Query Block list", which prevents somearbitrary machine from registering the DNS name of WPAD. This is a good security feature, as it prevents someone from just joining your network, and setting himself up asa proxy. The dynamic update feature of Domain Name System (DNS) makes it possible for DNS client computers toregister and dynamically update their resource records with a DNS server whenever a client changes itsnetwork address or host name. This reduces the need for manual administration of zone records. This convenience comes at a cost, however,because any authorized client can register any unused host name, even a host name that might havespecial significance for certain Applications. This can allow a malicious user to take over a special nameand divert certain types of network traffic to that user’s computer. Two commonly deployed protocols are particularly vulnerable to this type of takeover: the Web ProxyAutomatic Discovery Protocol (WPAD) and the Intra-site Automatic Tunnel Addressing Protocol (ISATAP). Even if a network does not deploy these protocols, clients that are configured to use them are vulnerable to thetakeover that DNS dynamic update enables. Most commonly, ISATAP hosts construct their PRLs by using DNS to locate a host named isatap on the localdomain.
For example, if the local domain is corp.contoso.com, an ISATAP-enabled host queries DNS to obtainthe IPv4 address of a host named
isatap.corp.contoso.com. In its default configuration, the Windows Server 2008 DNS Server service maintains a list of names that, ineffect, it ignores when it receives a query to resolve the name in any zone for which the server is authoritative. Consequently, a malicious user can spoof an ISATAP router in much the same way as a malicious user canspoof a WPAD server: A malicious user can use dynamic update to register the user’s own computer as acounterfeit ISATAP router and then divert traffic between ISATAP-enabled computers on the network. The initial contents of the block list depend on whether WPAD or ISATAP is already deployed when you addthe DNS server role to an existing Windows Server 2008 deployment or when you upgrade an earlier versionof Windows Server running the DNS Server service.
Add- DnsServerResourceRecord – The Add-DnsServerResourceRecordcmdlet adds a resource record for aDomain Name System (DNS) zone on a DNS server. You can add different types of resource records. Use different switches for different record types. By using this cmdlet, you can change a value for a record, configure whether a record has a time stamp,whether any
authenticated user can update a record with the same owner name, and change lookup
timeoutvalues, Windows Internet Name Service (WINS) cache settings, and replication settings. Set-DnsServerGlobalQueryBlockList – The Set-
DnsServerGlobalQueryBlockListcmdlet changes settingsof a global query block list on a Domain Name System (DNS) server. This cmdlet replaces all names in the list of names that the DNS server does not resolve with the names thatyou specify. If you need the DNS server to resolve names such as ISATAP and WPAD, remove these names from the list. Web Proxy Automatic Discovery Protocol (WPAD) and Intra-site Automatic Tunnel Addressing Protocol(ISATAP) are two commonly deployed protocols that are particularly vulnerable to hijacking.
http://technet.microsoft.com/en-us/library/jj649857(v=wps.620).aspx
http://technet.microsoft.com/en-us/library/cc794902%28v=ws.10%29.aspx
http://technet.microsoft.com/en-us/security/bulletin/ms09-008
http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2009-0093
Windows DNS Server in Microsoft Windows 2000 SP4, Server 2003 SP1 and SP2, and Server 2008, whendynamic updates are enabled, does not restrict registration of the "wpad" hostname, which allows remoteauthenticated users to hijack the Web Proxy AutoDiscovery (WPAD) feature, and conduct man-in-the-middleattacks by spoofing a proxy server, via a Dynamic Update request for this hostname, aka "DNS ServerVulnerability in WPAD Registration Vulnerability," a related issue to CVE- 2007-1692.
QUESTION 133
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1 that runs Windows Server 2012 R2 and has the Remote Access server role installed.
A user named User1 must connect to the network remotely. The client computer of User1 requires Challenge Handshake Authentication Protocol (CHAP) for remote connections.
CHAP is enabled on Server1.
You need to ensure that User1 can connect to Server1 and authenticate to the domain.
What should you do from Active Directory Users and Computers?
A. From the properties of Server1, select Trust this computer for delegation to any service (Kerberos only).
B. From the properties of Server1, assign the Allowed to Authenticate permission to User1.
C. From the properties of User1, select Use Kerberos DES encryption types for this account.
D. From the properties of User1, select Store password using reversible encryption.
Answer: D
Explanation:
The Store password using reversible encryption policy setting provides support for Applications that useprotocols that require the user’s password for authentication. Storing encrypted passwords in a way that isreversible means that the encrypted passwords can be decrypted. A knowledgeable attacker who is able tobreak this encryption can then log on to network resources by using the compromised account. For this reason,never enable Store password using reversible encryption for all users in the domain unless Applicationrequirements outweigh the need to protect password information. If you use the Challenge Handshake Authentication Protocol (CHAP) through remote access or InternetAuthentication Services (IAS), you must enable this policy setting.
CHAP is an authentication protocolthat is used by remote access and network connections.
Digest Authentication in Internet Information Services(IIS) also requires that you enable this policy setting. If your organization uses CHAP through remote access or IAS, or Digest Authentication in IIS, you mustconfigure this policy setting to Enabled. This presents a security risk when you Apply the setting through GroupPolicy on a user-by-user basis because it requires the appropriate user account object to be opened in ActiveDirectory Users and Computers.
http://technet.microsoft.com/pt-pt/library/hh994559%28v=ws.10%29.aspx
QUESTION 134
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed. Server1 has a virtual switch named RDS Virtual.
You replace all of the network adapters on Server1 with new network adapters that support single-root I/O visualization (SR-IOV).
You need to enable SR-IOV for all of the virtual machines on Server1.
Which two actions should you perform? (Each correct answer presents part of the solution.
Choose two.)
A. On each virtual machine, modify the Advanced Features settings of the network adapter.
B. Modify the settings of the RDS Virtual virtual switch.
C. On each virtual machine, modify the BIOS settings.
D. Delete, and then recreate the RDS Virtual virtual switch.
E. On each virtual machine, modify the Hardware Acceleration settings of the network adapter.
Answer: DE
Explanation:
The first step when allowing a virtual machine to have connectivity to a physical network is to create an external virtual switch using Virtual Switch Manager in Hyper-V Manager. The additional step that is necessary when using SR-IOV is to ensure the checkbox is checked when the virtual switch is being created. It is not possible to change a "non SR-IOV mode" external virtual switch into an "SR-IOV mode" switch. The choice must be made a switch creation time.
E: Once a virtual switch has been created, the next step is to configure a virtual machine. SR-IOV in Windows Server "8" is supported on x64 editions of Windows "8" as a guest operating system (as in Windows "8" Server, and Windows "8" client x64, but not x86 client). We have rearranged the settings for a virtual machine to introduce sub-nodes under a network adapter, one of which is the hardware acceleration node. At the bottom is a checkbox to enable SR-IOV.
Note:
* Steps:
/ SR-IOV must be enabled on virtual switch
/ Install additional network drivers in the guest OS
/ Enable SR-IOV within the VMs though Hyper-V Manager
* Single Root I/O Virtualization (SR-IOV) is a standard introduced by the PCI-SIG that owns and manages PCI specifications as open industry standards.
SR-IOV enables network traffic to bypass the software switch layer of the Hyper-V Virtualization stack to reduce the I/O overhead in this layer. It allows an SR-IOV virtual function of a physical network adapter to be assigned directly to a virtual machine to increase network throughput by reducing latency. Host CPU overhead also get reduced for processing network traffic.
* The diagram below illustrates how SR-IOV allows virtual machines to directly address the physical NIC.
Reference: Everything you wanted to know about SR-IOV in Hyper-V Part 5
QUESTION 135
Your network contains a server named Server1 that runs Windows Server 2012 R2. Server1 is a member of a workgroup.
You need to configure a local Group Policy on Server1 that will apply only to non- administrators.
Which tool should you use?
A. Server Manager
B. Group Policy Management Editor
C. Group Policy Management
D. Group Policy Object Editor
Answer: D
Explanation:
http://technet.microsoft.com/en-us/library/cc766291%28v=ws.10%29.aspx
QUESTION 136
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server! that runs Windows Server 2012 R2.
Server1 contains a virtual machine named VM1 that runs Windows Server 2012 R2.
You need to ensure that a user named User1 can install Windows features on VM1.
The solution must minimize the number of permissions assigned to User1.
To which group should you add User1?
A. Administrators on VM1
B. Power Users on VM1
C. Hyper-V Administrators on Server1
D. Server Operators on Server1
Answer: A
Explanation:
In Windows Server 2012 R2, the Server Manager console and Windows PowerShell-cmdlets for ServerManager allow installation of roles and features to local or remote servers, or offline virtual hard disks (VHDs).
You can install multiple roles and features on a single remote server or offline VHD in a single Add Roles andFeatures Wizard or Windows PowerShell session. You must be logged on to a server as an administrator to install or uninstall roles, role services, andfeatures. If you are logged on to the local computer with an account that does not have administrator rights onyour target server, right-click the target server in the Servers tile, and then click Manage As to provide anaccount that has administrator rights. The server on which you want to mount an offline VHD must be added toServer Manager, and you must have Administrator rights on that server.
http://technet.microsoft.com/en-us/library/hh831809.aspx
QUESTION 137
Your network contains an Active Directory domain named adatum.com. The domain contains a member server named LON-DC1. LON-DC1 runs Windows Server 2012 R2 and has the DHCP Server server role installed. The network contains 100 client computers and 50 IP phones. The computers and the phones are from the same vendor.
You create an IPv4 scope that contains addresses from 172.16.0.1 to 172.16.1.254.
You need to ensure that the IP phones receive IP addresses in the range of 172.16.1.100 to 172.16.1.200. The solution must minimize administrative effort.
What should you create?
A. Server level policies
B. Filters
C. Reservations
D. Scope level policies
Answer: D
Explanation:
When a client matches the conditions of a policy, the DHCP server responds to the clients based on the settings of a policy.
Settings associated to a policy can be an IP address range and/or options.
An administrator could configure the policy to provide an IP address from a specified sub-range within the overall IP address range of the scope.
You can also provide different option values for clients satisfying this policy.
Policies can be defined server wide or for a specific scope.
A server wide policy – on the same lines as server wide option values – is applicable to all scopes on the DHCP server.
A server wide policy however cannot have an IP address range associated with it.
There a couple of ways to segregate clients based on the type of device. One way to do this is by using vendor class/identifier. This string sent in option 60 by most DHCP clients identify the vendor and thereby the type of the device.
Another way to segregate clients based on device type is by using the MAC address prefix. The first three bytes of a MAC address is called OUI and identify the vendor or manufacturer of the device.
By creating DHCP policies with conditions based on Vendor Class or MAC address prefix, you can now segregate the clients in your subnet in such a way, that devices of a specific type get an IP address only from a specified IP address range within the scope. You can also give different set of options to these clients.
In conclusion, DHCP policies in Windows Server 2012 R2 enables grouping of clients/devices using the different criteria and delivering targeted network configuration to them.
Policy based assignment in Windows Server 2012 R2 DHCP allows you to create simple yet powerful rules to administer DHCP on your network.
QUESTION 138
Your network contains an Active Directory forest. The forest contains a single domain named contoso.com. The domain contains four domain controllers.
The domain controllers are configured as shown in the following table. 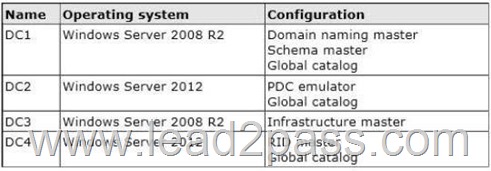
You plan to deploy a new domain controller named DC5 in the contoso.com domain.
You need to identify which domain controller must be online to ensure that DC5 can be promoted successfully to a domain controller.
Which domain controller should you identify?
A. DC1
B. DC2
C. DC3
D. DC4
Answer: D
Explanation:
Relative ID (RID) Master:
Allocates active and standby RID pools to replica domain controllers in the same domain. (corp.contoso.com) Must be online for newly promoted domain controllers to obtain a local RID pool that is required to advertise or when existing domain controllers have to update their current or standby RID pool allocation.
The RID master is responsible for processing RID pool requests from all domain controllers in a particular domain. When a DC creates a security principal object such as a user or group, it attaches a unique Security ID (SID) to the object.
This SID consists of a domain SID (the same for all SIDs created in a domain), and a relative ID (RID) that is unique for each security principal SID created in a domain. Each DC in a domain is allocated a pool of RIDs that it is allowed to assign to the security principals it creates.
When a DC’s allocated RID pool falls below a threshold, that DC issues a request for additional RIDs to the domain’s RID master. The domain RID master responds to the request by retrieving RIDs from the domain’s unallocated RID pool and assigns them to the pool of the requesting DC At any one time, there can be only one domain controller acting as the RID master in the domain.
The Infrastructure Master – The purpose of this role is to ensure that cross-domain objectreferences are correctly handled. For example, if you add a user from one domain to a security group from a different domain, the Infrastructure Master makes sure this is done properly. As you can guess however, if your Active Directory deployment has only a single domain, then the Infrastructure Master role does no work at all, and even in a multi-domain environment it is rarely used except when complex user administration tasks are performed, so the machine holding this role doesn’t need to have much horsepower at all.
http://support.microsoft.com/kb/223346
http://en.wikipedia.org/wiki/Flexible_single_master_operation
QUESTION 139
You have a server named Server 1. Server1 runs Windows Server 2012 R2.
Server1 has a thin provisioned disk named Disk1.
You need to expand Disk1.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. From File and Storage Services, extend Disk1.
B. From File and Storage Services, add a physical disk to the storage pool.
C. From Disk Management, extend the volume.
D. From Disk Management, delete the volume, create a new volume, and then format the volume.
E. From File and Storage Services, detach Disk1.
Answer: AB
Explanation:
Step 1 (B): if required add physical disk capacity.
Step 2 (A): Dynamically extend the virtual disk (not volume). Windows Server 2012 Storage Space subsystem now virtualizes storage by abstracting multiple physical disksinto a logical construct with specified capacity. The process is to group selected physical disks into a container,the so-called storage pool, such that the total capacity collectively presented by those associated physicaldisks can appear and become manageable as a single and seemingly continuous space. Subsequently astorage administrator creates a virtual disk based on a storage pool, configure a storage layout which isessentially a RAID level, and expose the storage of the virtual disk as a drive letter or a mapped folder inWindows Explorer.
The system administrator uses File and Storage Services in Server Manager or the Disk Management tool torescan the disk, bring the disk online, and extend the disk size.
http://blogs.technet.com/b/yungchou/archive/2012/08/31/windows-server-2012-storagevirtualization-explained.aspx
QUESTION 140
Your network contains an Active Directory domain named contoso.com.
The domain contains a member server named HVServer1.
HVServer1 runs Windows Server 2012 R2 and has the Hyper-V server role installed.
HVServer1 hosts two virtual machines named Server1 and Server2.
Both virtual machines connect to a virtual switch named Switch1.
On Server2, you install a network monitoring application named App1.
You need to capture all of the inbound and outbound traffic to Server1 by using App1.
Which two commands should you run from Windows PowerShell? (Each correct answer presents part of the solution. Choose two.)
A. Get-VM "Server2" | Set-VMNetworkAdapter -IovWeight 1
B. Get-VM "Server1" | Set-VMNetworkAdapter -Allow/Teaming On
C. Get-VM "Server1" | Set-VMNetworkAdapter -PortMirroring Source
D. Get-VM "Server2" | Set-VMNetworkAdapter -PortMirroring Destination
E. Get-VM "Server1" | Set-VMNetworkAdapter -IovWeight 0
F. Get-VM "Server2" | Set-VMNetworkAdapter-AllowTeaming On
Answer: CD
Explanation:
C: Catching the traffic from Server1
D: Catching the traffic to Server1.
Note:
* Get-VM
Gets the virtual machines from one or more Hyper-V hosts.
-ComputerName<String[]>
Specifies one or more Hyper-V hosts from which virtual machines are to be retrieved. NetBIOS names, IP addresses, and fully-qualified domain names are allowable. The default is the local computer — use "localhost" or a dot (".") to specify the local computer explicitly.
* Set-VMNetworkAdapter
Configures features of the virtual network adapter in a virtual machine or the management operating system.
* -PortMirroring<VMNetworkAdapterPortMirroringMode>
Specifies the port mirroring mode for the network adapter to be configured. Allowed values are None, Source, and Destination. If a virtual network adapter is configured as Source, every packet it sends or receives is copied and forwarded to a virtual network adapter configured to receive the packets. If a virtual network adapter is configured as Destination, it receives copied packets from the source virtual network adapter. The source and destination virtual network adapters must be connected to the same virtual switch. Specify None to disable the feature.
Reference: Set-VMNetworkAdapter; Get-VM
http://technet.microsoft.com/en-us/library/hh848479%28v=wps.620%29.aspx http://technet.microsoft.com/en-us/library/hh848457%28v=wps.620%29.aspx
More new updated 70-410 brain dumps in pdf and vce format can free download on Lead2pass.com. By training the new updated questions and answers, you will pass the exam easily.