Free Download Cisco 350-001 VCE Test Engine Full Version Now (191-200)
QUESTION 191
Half of your network uses RIPv2 and the other half runs OSPF. The networks do not communicate
with each other. Which two of these factors describe the impact of activating EIGRP over each
separate part? (Choose two.)
A. EIGRP will not be accepted when configured on the actual RIPv2 routers.
B. OSPF will no longer be used in the routing table, because you only have EIGRP internal routes
running.
C. OSPF will no longer be used in the routing table, because you only have EIGRP external routes
running.
D. RIPv2 will populate its RIP database but not its routing table, because you only have EIGRP
external routes running.
E. RIPv2 will populate its RIP database but not its routing table, because you only have EIGRP
internal routes running.
F. OSPF database will have RIPv2 routes.
Answer: BE
Explanation:
http://www.cisco.com/en/US/tech/tk365/technologies_tech_note09186a00800943c5.shtml
QUESTION 192
Your company is researching a new application that runs over IPv6, but part of it must still have IPv4 support. Your company uses a traditional IPv4 network. Your plan is not to run IPv6 over the whole network, but to segment parts of the network or even to operate simultaneously with IPv6
and IPv4. You must make a brief presentation about IPv6 technology to the board of technical
directors. Which three of these items could be part of your presentation? (Choose three.)
A. Tunnel IPv6 over IPv4 to connect far-end IPv6 networks.
B. Explain why configuring IPv4 and IPv6 at the same time over the same LAN interface is not
possible.
C. Explain why configuring IPv4 and IPv6 at the same time over the same LAN interface is possible.
D. What is the meaning of EUI-64 and how does it work?
E. Tunnel IPv4 over IPv6 to connect far-end IPv4 networks.
Answer: ACD
Explanation:
An interface ID is used to identify interfaces on a link. The interface ID must be unique to the link. It may also be unique over a broader scope. In many cases, an interface ID will be the same as or based on the link-layer address of an interface. Interface IDs used in aggregatable global unicast and other IPv6 address types must be 64 bits long and constructed in the modified EUI-64 format. Interface IDs are constructed in the modified EUI-64 format in one of the following ways:
For all IEEE 802 interface types (for example, Ethernet, and FDDI interfaces), the first three octets (24 bits) are taken from the Organizationally Unique Identifier (OUI) of the 48-bit link-layer address (the Media Access Control [MAC] address) of the interface, the fourth and fifth octets (16 bits) are a fixed hexadecimal value of FFFE, and the last three octets (24 bits) are taken from the last three octets of the MAC address. The construction of the interface ID is completed by setting the Universal/Local (U/L) bit the seventh bit of the first octet a value of 0 or 1. A value of 0 indicates a locally administered identifier; a value of 1 indicates a globally unique IPv6 interface identifier.
For other interface types (for example, serial, loopback, ATM, Frame Relay, and tunnel interface types except tunnel interfaces used with IPv6 overlay tunnels), the interface ID is constructed in the same way as the interface ID for IEEE 802 interface types; however, the first MAC address from the pool of MAC addresses in the router is used to construct the identifier (because the interface does not have a MAC address).
For tunnel interface types that are used with IPv6 overlay tunnels, the interface ID is the IPv4 address assigned to the tunnel interface with all zeros in the high-order 32 bits of the identifier. An IPv4-compatible IPv6 address is an IPv6 unicast address that has zeros in the high-order 96 bits of the address and an IPv4 address in the low-order 32 bits of the address. The format of an IPv4- compatible IPv6 address is 0:0:0:0:0:0:A.B.C.D or ::A.B.C.D. The entire 128-bit IPv4-compatible IPv6 address is used as the IPv6 address of a node and the IPv4 address embedded in the low-order 32 bits is used as the IPv4 address of the node. IPv4-compatible IPv6 addresses are assigned to nodes that support both the IPv4 and IPv6 protocol stacks and are used in automatic tunnels.
QUESTION 193
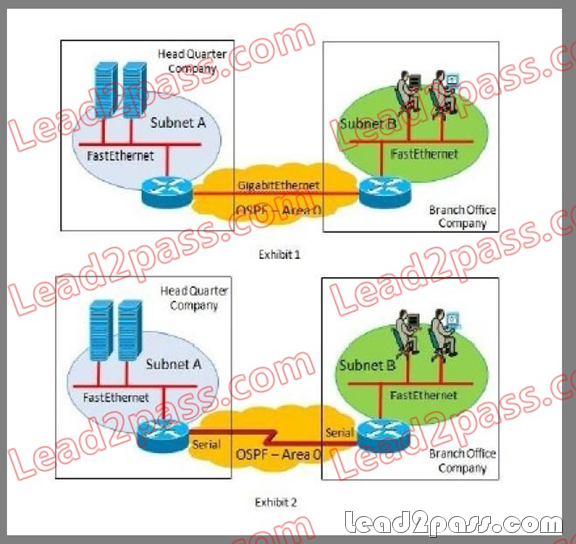
Refer to exhibits 1 and 2. In exhibit 1, all users on the LAN segment use router A as the active HSRP router. Router B is the standby router for the HSRP. In exhibit 2, the network management
team reported that there is no utilization on the WAN link B. To solve this problem, you decide to change the logical topology of your LAN, but you are not sure about what changes must be made.
You must manage HSRP or change it to another protocol in order to provide the most scalable
design, automatic redundancy, and load balancing. Which one of these actions would be the best
choice?
A. Use MHSRP, with three users using router A as the default gateway and three users using router
B as the default gateway.
B. Keep HSRP and activate PBR to redirect half of the traffic to the other WAN link.
C. Use the backup interface on the WAN link B to provide load balancing for all users.
D. Use GLBP instead, because it provides you with up to three MAC addresses for the same default
gateway virtual IP address.
E. Use GLBP instead, because it provides you with up to four MAC addresses for the same default
gateway virtual IP address.
Answer: E
Explanation:
In HSRP and VRRP, only the primary router is used to forward traffic, others routers must wait for the primary one down before they are used. Also, the bandwidth of the standby (and other) routers are not used and wasted. With GLBP, up to four gateways can be used simultaneously. There is still one virtual IP address in a group, but GLBP can automatically select which router in the group to forward traffic by sending the virtual MAC address of a selected router to that host.
QUESTION 194
Refer to exhibits 1 and 2. A company uses a Metro Ethernet (Gigabit Ethernet) dedicated circuit to communicate between users (subnet B) and servers (subnet A) as shown in Exhibit 1. Both
routers use OSPF to advertise the subnets. During a weekly management meeting, they realize
that the WAN link is oversize. They have been using only 2 Mb/s in the worst-case scenario. So
they propose a new, cheaper WAN connection using a 2-Mb/s Frame-Relay point-to-point link to
interconnect both sites (Exhibit 2). The Frame Relay service provider informs them that multicast traffic is not allowed to run over the service provider network. Which one of these options is best to enable the company to establish the OSPF neighbor adjacency?
A. Use OSPF network broadcast, because it uses unicast to establish a neighbor relationship.
B. Use OSPF network point-to-multipoint, because it uses unicast to establish a neighbor
relationship.
C. Use OSPF network point-to-point, because it uses unicast to establish a neighbor relationship.
D. Use OSPF network point-to-multipoint nonbroadcast, because it establishes a neighbor
relationship using unicast packets.
E. Use OSPF network nonbroadcast, because it establishes a neighbor relationship using multicast.
Answer: D
Explanation:
OSPF Point-to-Multipoint Network with Separate Costs per Neighbor Description
OSPF has two new features related to point-to-multipoint networks. One feature applies to broadcast networks; the other feature applies to nonbroadcast networks. On point-to-multipoint, broadcast networks, there is no need to specify neighbors. However, you can specify neighbors with the neighbor command, in which case you should specify a cost to that neighbor.
On point to multipoint, nonbroadcast networks, you now use the neighbor command to identify neighbors.
Assigning a cost to a neighbor is optional.
Before this feature, some OSPF point-to-multipoint protocol traffic was treated as multicast traffic. Therefore, the neighbor command was not needed for point-to-multipoint interfaces because multicast took care of the traffic. Hellos, updates and acknowledgments were sent using multicast. In particular, multicast hellos discovered all neighbors dynamically. However, some customers were using point-to-multipoint on nonbroadcast media (such as classic IP over ATM), so their routers could not dynamically discover their neighbors. This feature allows the neighbor command to be used on point-to-multipoint interfaces. On any point-to-multipoint interface (broadcast or not), the Cisco IOS software assumed the cost to each neighbor was equal. The cost was configured with the ip ospf cost command. In reality, the bandwidth to each neighbor is different, so the cost should be different. With this feature, you can configure a separate cost to each neighbor. This feature applies to point-to-multipoint interfaces only.
Benefits
You can now configure neighbors on point-to-multipoint interfaces and assign a cost to each neighbor. These capabilities allow the router to dynamically discover neighbors over nonbroadcast media and to prefer some routes over others by assigning different costs to neighbors.
http://www.cisco.com/en/US/docs/ios/11_3/feature/guide/ospfpmp.html
QUESTION 195
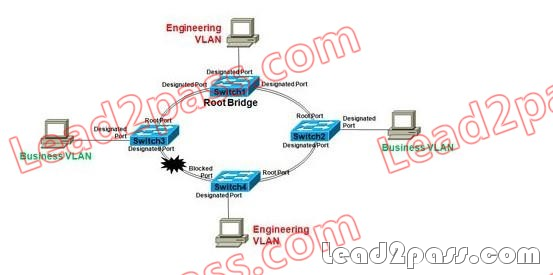
Refer to the exhibit. Users from the Engineering VLAN complain that every time Business VLAN
users have a network connectivity issue, the Engineering VLAN users usually have problems
experiencing slow response or network connectivity problems. After troubleshooting, an
unauthorized switch 2 was found. This unauthorized switch has been a regular problem, assuming
the root bridge function under the spanning-tree domain and causing the Engineering VLAN to be
unstable. Which three of these actions could be suggested to fix the problem?
A. Upgrade Spanning Tree Protocol to Rapid Spanning Tree Protocol.
B. Change Business VLAN PCs to switch 1 and switch 4.
C. Force the root bridge to be switch 2, instead.
D. Adjust spanning-tree timers (max-age and forward-delay).
E. Shut down all unused ports.
F. Use MSTP to separate the Engineering VLAN from the Business VLAN to optimize spanning-tree
convergence time within each VLAN
Answer: AEF
Explanation:
The best action is to shut down unused ports and use MSTP to separate Engineering VLAN from the business VLAN so that spanning-tree convergence time can be optimized within each VLAN. Also upgrade spanning tree protocol to Rapid spanning tree protocol (RSTP).
QUESTION 196
When running IP SLA, which application type should be used if you want to know round-trip delay, jitter, and packet loss for the full path?
A. ICMP path echo
B. UDP echo
C. ICMP path jitter
D. Application Performance Monitor
E. TCP connect
Answer: C
Explanation:
Before configuring any IP SLAs application, you can use the show ip sla application command to verify that the operation type is supported on your software image. In contrast with other IP SLAs operations, the IP SLAs Responder does not have to be enabled on either the target device or intermediate devices for Path Jitter operations. However, the operational efficiency may improve if you enable the IP SLAs Responder. The IP SLAs ICMP Path Jitter operation is ICMP-based. ICMP- based operations can compensate for source processing delay but cannot compensate for target processing delay. For more robust monitoring and verifying, use of the IP SLAs UDP Jitter operation is recommended. The jitter values obtained using the ICMP Path Jitter operation are approximates because ICMP does not provide the capability to embed processing times on routers in the packet. If the target router does not place ICMP packets as the highest priority, then the router will not respond properly. ICMP performance also can be
affected by the configuration of priority queueing on the router and by ping response. The path jitter operation does not support hourly statistics and hop information. Unlike other IP SLAs operations, the ICMP Path Jitter operation is not supported in the RTTMON MIB. Path Jitter operations can only be configured using Cisco IOS commands and statistics can only be returned using the show ip sla commands. The IP SLAs Path Jitter operation does not support the IP SLAs History feature (statistics history buckets) because of the large data volume involved with Jitter operations.
QUESTION 197
Which option is true when calculating round-trip delay in IP SLA operations?
A. The processing time on the end routers is only assessed for operations that involve the responder.
B. The processing time on the end routers is only assessed for operations that involve the
transmitter.
C. The processing time on the end routers is only assessed for operations that involve both the
responder and the transmitter.
D. The processing time on the end routers is not assessed for neither the responder nor the
transmitter.
Answer: A
Explanation:
The Cisco IOS IP SLAs Responder is a component embedded in the destination Cisco routing device that allows the system to anticipate and respond to Cisco IOS IP SLAs request packets. The Cisco IOS IP SLAs Responder provides an enormous advantage with accurate measurements without the need for dedicated probes and additional statistics not available via standard ICMP-based measurements. The patented Cisco IOS IP SLAs Control Protocol is used by the Cisco IOS IP SLAs Responder providing a mechanism through which the responder can be notified on which port it should listen and respond. Only a Cisco IOS device can be a source for a destination IP SLAs Responder. Figure 2 shows where the Cisco IOS IP SLAs Responder fits in relation to the IP network. The Cisco IOS IP SLAs Responder listens on a specific port for control protocol messages sent by a Cisco IOS IP SLAs operation. Upon receipt of the control message, the responder will enable the specified UDP or TCP port for the specified duration. During this time, the responder accepts the requests and responds to them. The responder disables the port after it responds to the Cisco IOS IP SLAs packet, or when the specified time expires. For added security, MD5 authentication for control messages is available.
Enabling the Cisco IOS IP SLAs Responder on the destination device is not required for all Cisco IOS IP SLAs operations. For example, if services that are already provided by the destination router (such as Telnet or HTTP) are chosen, the Cisco IOS IP SLAs Responder need not be enabled. For non-Cisco devices, the Cisco IOS IP SLAs Responder cannot be configured and Cisco IOS IP SLAs can send operational packets only to services native to those devices.
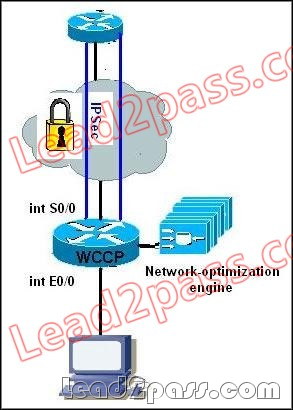
QUESTION 198
Refer to the exhibit. You are asked to enable redirection for a network optimization engine that will be connected directly to your company CPE. What is the correct configuration to enable
redirection for traffic optimization?
A. (config)#interface s0/0
(config-if)#ip wccp 61 out
(config)#interface e0/0
(config-if)#ip wccp 62 out
B. (config)#interface s0/0
(config-if)#ip wccp 62 in
(config)#interface e0/0
(config-if)#ip wccp 61 in
C. (config)#interface s0/0
(config-if)#ip wccp 61 in
(config-if)#ip wccp 62 out
D. (config)#interface e0/0
(config-if)#ip wccp 61 in
(config-if)#ip wccp 62 out
E. (config)#interface e0/0
(config-if)#ip wccp 61 out
(config-if)#ip wccp 62 in
F. (config)#interface s0/0
(config-if)#ip wccp 61 out
(config-if)#ip wccp 62 in
Answer: D
Explanation:
Configuring WCCP for redirection for inbound traffic on interfaces allows you to avoid the overhead associated with CEF forwarding for outbound traffic. Setting an output feature on any interface results in the slower switching path of the feature being taken by all packets arriving at all interfaces. Setting an input feature on an interface results in only those packets arriving at that interface taking the configured feature path; packets arriving at other interfaces will use the faster default path. Configuring WCCP for inbound traffic also allows packets to be classified before the routing table lookup, which translates into faster redirection of packets.
QUESTION 199
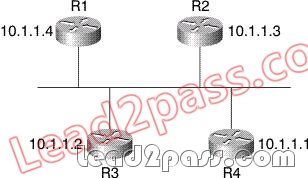
Refer to the exhibit. A network engineer has connected a packet-capturing device to the common broadcast segment in this network, on which all the routers are configured to run OSPF. By examining various show commands on the routers, the engineer discovers that the designated router is R1. By examining the captured packets, the engineer also discovers that every new LSA that R3 sends to the link, R1 resends to the link a few moments later.
Is this correct OSPF operation, and why or why not?
A. This is correct operation; flooding new LSA information to the other routers is a function of the designated router.
B. This is incorrect operation; each new LSA should only be flooded onto a given broadcast link once.
C. This is correct operation; OSPF uses a scheme whereby each LSA flooded onto a link is acknowledged by the receiving router through a reflood back onto the link of the same information.
D. This is incorrect operation; it indicates that while R3 can send packets to R1, R1 cannot send packets to R3.
Answer: A
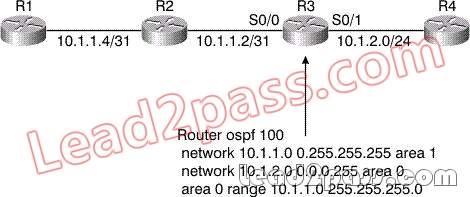
QUESTION 200
Refer to the exhibit. In this network, what will be the impact at R4 if the link between R1 and R2 fails?
A. R3 will generate a new summary (type 3) LSA when the link between R1 and R2 fails. When R4 receives this new summary LSA, it will run SPF, recalculating its shortest path tree.
B. R4 will not receive any new LSAs of any type, nor will it run SPF.
C. R4 will receive a router (type 1) LSA from R2, since it has lost its connection to R2. When R4 receives this LSA, it will run SPF to recalculate the shortest path tree.
D. R2 will generate a new network (type 2) LSA, since it has lost its connection to 10.1.1.4/30. When R4 receives this LSA, it will run SPF to recalculate the shortest path three.
Answer: B
If you want to pass Cisco 350-001 exam successfully, donot missing to read latest lead2pass Cisco 350-001 practice tests.
If you can master all lead2pass questions you will able to pass 100% guaranteed.