[PDF&VCE] Pass 200-355 Exam By Exercising Lead2pass Latest 200-355 VCE And PDF Dumps (256-280)
2016 September Cisco Official New Released 200-355 Dumps in Lead2pass.com!
100% Free Download! 100% Pass Guaranteed!
Lead2pass updates Cisco 200-355 exam questions, adds some new changed questions from Cisco Official Exam Center. Want to know 2016 200-355 exam test points? Download the following free Lead2pass latest exam questions today!
Following questions and answers are all new published by Cisco Official Exam Center: http://www.lead2pass.com/200-355.html
QUESTION 256
Which encryption algorithm does WPA use?
A. RC4
B. DES
C. AES
D. DH5
Answer: A
Explanation:
The RC4 Encryption Algorithm, developed by Ronald Rivest of RSA, is a shared key stream cipher algorithm requiring a secure exchange of a shared key. The symmetric key algorithm is used identically for encryption and decryption such that the data stream is simply XORed with the generated key sequence. The algorithm is serial as it requires successive exchanges of state entries based on the key sequence. Hence implementations can be very computationally intensive. The RC4 encryption algorithm is used by standards such as IEEE 802.11 within WEP (Wireless Encryption Protocol) using 40 and 128-bit keys. Published procedures exist for cracking the security measures as implemented in WEP.
http://www.vocal.com/cryptography/rc4-encryption-algoritm/
QUESTION 257
Which statement about configuration of Layer 2 wireless user authentication on a Cisco WLC is true?
A. Local EAP is used only if an external RADIUS is not configured or is unreachable.
B. The external RADIUS is used only if local EAP is not configured.
C. The administrator chooses whether local EAP or an external RADIUS is used first.
D. The external RADIUS is used only if local EAP is explicitly disabled.
Answer: A
Explanation:
If any RADIUS servers are configured on the controller, the controller tries to authenticate the wireless clients using the RADIUS servers first. Local EAP is attempted only if no RADIUS servers are found, either because the RADIUS servers timed out or no RADIUS servers were configured. If four RADIUS servers are configured, the controller attempts to authenticate the client with the first RADIUS server, then the second RADIUS server, and then local EAP. If the client attempts to then reauthenticate manually, the controller tries the third RADIUS server, then the fourth RADIUS server, and then local EAP.
http://www.cisco.com/c/en/us/td/docs/wireless/controller/7-4/configuration/guides/consolidated/b_cg74_CONSOLIDATED/b_cg74_CONSOLIDATED_chapter_0110010.html
QUESTION 258
Refer to the exhibit. Which option must be chosen if only the WPA is needed? 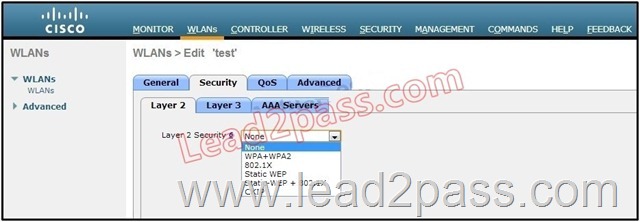
A. WPA+WPA2
B. Static-WEP + 802.1X
C. 802.1X
D. CKIP
Answer: A
Explanation:
Wi-Fi Protected Access (WPA) and Wi-Fi Protected Access II (WPA2) are two security protocols and security certification programs developed by the Wi-Fi Alliance to secure wireless computer networks.
http://en.wikipedia.org/wiki/Wi-Fi_Protected_Access
QUESTION 259
Which statement describes a security weakness of a WPA2 with a PSK?
A. The compromised key can be used for another connection.
B. The key can be eavesdropped from the wireless medium.
C. The key can be recreated from a few eavesdropped frames.
D. The key is not case-sensitive and is vulnerable to compromise by brute-force methods.
Answer: A
Explanation:
WPA2-Enterprise is (in my opinion) considerably more secure than PSK.
QUESTION 260
To implement a more secure means of communication for voice and data, what technology successfully resists interference by utilizing a wider bandwidth than needed for the transmitting signal?
A. Spread Spectrum
B. Microwave
C. Extended U-NII2
D. ISM Bands
Answer: A
QUESTION 261
An 802.11g network is experiencing intermittent signal degradation and Spectrum Analyzer is being used to try and locate the problem. What two interferers would likely be identified? (Choose two.)
A. multiple cell phones
B. microwave oven
C. FM Radio
D. cordless phone
E. document scanner
Answer: BD
QUESTION 262
A wireless bridge is being installed near an airport. An organization informs the city council about complying with max power levels that could be used and settings on any 5GHz channels used that might interfere with the airport radar. What organization is this?
A. Institute of Electrical and Electronics Engineers
B. Internet Engineering Task Force
C. Federal Communications Commission
D. Wireless Fidelity Alliance
Answer: C
QUESTION 263
An installation uses a 21dBi parabolic dish. It is connected to the 802.11n radio via low loss antenna coax rated at 4dB loss/100 feet. After testing, it has been determined that 2mW of power will be lost in the cable. An EIRP producing 200mW is desired. What should the transmit power be set to?
A. 8mW
B. 3dBm
C. 3.16mW
D. 5mW
Answer: C
QUESTION 264
An engineer is seeing a pattern closest to that of an Isotropic Radiator. What other antenna will produce a similar pattern?
A. 5 dBi patch
B. 13.5 dBi Yagi
C. 2.2 dBi omni
D. 21 dBi parabolic
Answer: C
QUESTION 265
When using multiple SSIDs on a lightweight AP, how does the traffic of each SSID reach the 802.3 network?
A. provide routing between them at the core so that the SSIDs can reach the internet
B. configure 802.11q trunking on the Ethernet switch port that is connected to the AP
C. configure ACLs at the switch port that will allow all desired SSIDs to pass traffic
D. configure the SSIDs on the WLC and it will regulate the traffic based on traffic type
Answer: B
QUESTION 266
Refer to the exhibit. Based on the diagram, what two design requirements must be met? (Choose two.) 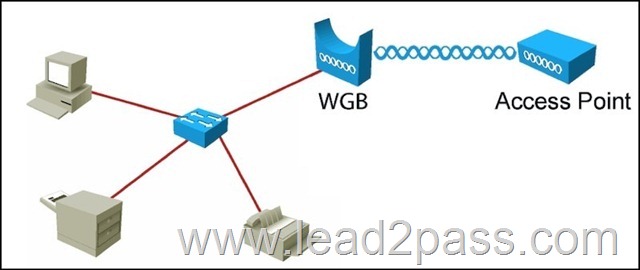
A. WGB is Autonomous
B. WGB is Universal
C. WGB can be Autonomous or Universal
D. Upstream AP is Aironet
E. Upstream AP is not Aironet
F. Upstream AP can be any make/model
Answer: AD
QUESTION 267
What 802.1x role is responsible for moving a port to the authorized state?
A. Supplicant
B. Authenticator
C. Authentication Server
D. RADIUS Server
Answer: B
QUESTION 268
How many types of control frames are only used in PCF mode?
A. 0
B. 1
C. 2
D. 3
E. 4
F. 5
Answer: D
QUESTION 269
An engineer is gathering information for a wireless survey of a hospital. What three pieces of information must be collected for an active survey to assess the outcome best suited for the facility? (Choose three.)
A. presence of microwave ovens
B. number of patients that are at the facility
C. utilization of Location Services or voice applications
D. floor plans of adjacent facilities
E. use of wireless for secure records
F. spectrum analysis to locate all the computer work stations
G. existing Network Switch types and model numbers
H. type of devices present on the new wireless network
Answer: ACH
QUESTION 270
A company wants to implement wireless in all 20 remote office locations and wants centralized management of these remote sites. What application would meet the requirements?
A. Control And Provisioning of Wireless Access Points
B. Cisco point- to multi-point wireless bridging
C. Cisco autonomous access points in FlexConnect mode
D. Split MAC architecture utilizing LWAPP and WLC
Answer: D
QUESTION 271
A customer mounted three new APs in a small business. After configuring the IP address, users still could not access the web through the new access points.
What two configurations are needed to fix this? (Choose two.)
A. Security parameters
B. Gateway address
C. Service Set ID
D. Antenna option
E. EAP Authentication
F. Unique AP Name
Answer: BC
QUESTION 272
A client is deploying lightweight APs. Those with LAN connections to the controller would be considered what mode of deployment, while access points deployed across a higher latency connection are deployed in what mode?
A. HREAP; Bridge
B. Local; Bridge
C. HREAP; Flex Connect
D. Local; Flex Connect
Answer: D
QUESTION 273
When using DHCP option 43, the discovery option supports vendor specific identifiers in order to obtain what IP address?
A. core router’s gateway
B. closest distribution switch
C. local WLAN controller
D. local Radius Server
Answer: C
QUESTION 274
Wireless clients are experiencing loss of connectivity while roaming between controllers. To fix this, what configuration should be the same on all controllers within the mobility group?
A. management interface IP address
B. IP address of the virtual interface
C. AP Manager interface IP address
D. IP address of the Service Port
Answer: B
QUESTION 275
What is a function of the service port on a WLC?
A. controls mobility manager communications on all physical ports
B. controls out-of-band management for system recovery and maintenance
C. controls communication with Cisco Aps
D. controls communications for all physical ports
Answer: B
QUESTION 276
What are three functions of RRM? (Choose three.)
A. dynamic channel assignment
B. detection and avoidance of interference
C. dynamic antenna polarization
D. dynamic transmit power control
E. dynamic controller selection
F. detection and avoidance of AP client load
Answer: ABD
QUESTION 277
What three components are required to configure Mobility Group Members between Wireless LAN Controllers? (Choose three.)
A. Controller Management IP Address
B. Controller Virtual IP Address
C. Controller Multicast IP Address
D. Controller MAC Address
E. Controller Mobility Group Name
F. Controller AP Management IP Address
G. Controller RF Group Name
Answer: ADE
QUESTION 278
What authentication method requires a certificate on both the client and authentication server?
A. PEAP
B. EAP-TLS
C. EAP-FAST
D. WPA-PSK
E. WEP
F. EAP-TTLS
Answer: B
QUESTION 279
An enterprise needs their iPhones to connect to the EAP-TLS network. How should the devices be configured?
A. push profile and certificate through Configuration Utility
B. configure directly through Settings application
C. email certificate to device then configure through Settings application
D. download certificate from web page then configure through Settings application
E. push profile and certificate through iTunes
Answer: A
QUESTION 280
What AnyConnect module can be used to provide a detailed scan list of the Wi-Fi environment?
A. DART
B. Telemetry
C. Web Security
D. NAM
E. Posture
Answer: A
Lead2pass promise that all 200-355 exam questions are the latest updated, we aim to provide latest and guaranteed questions for all certifications. You just need to be braved in trying then we will help you arrange all later things! 100% pass all exams you want or full money back! Do you want to have a try on passing 200-355?
200-355 new questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDS2dtNHE0NWQwQzQ
2016 Cisco 200-355 exam dumps (All 410 Q&As) from Lead2pass:
http://www.lead2pass.com/200-355.html [100% Exam Pass Guaranteed]