[PDF&VCE] 2016 Exam 400-101 Dumps From Lead2pass Cover All New 400-101 New Questions (826-850)
2016 October Cisco Official New Released 400-101 Dumps in Lead2pass.com!
100% Free Download! 100% Pass Guaranteed!
2016 get prepared with fully updated Cisco 400-101 real exam questions and accurate answers for 400-101 exam. Lead2pass IT experts review the 400-101 newly added questions and offer correct Cisco 400-101 exam questions answers. 100% pass easily!
Following questions and answers are all new published by Cisco Official Exam Center: http://www.lead2pass.com/400-101.html
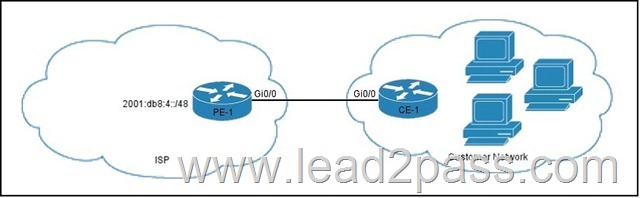
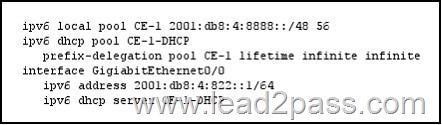
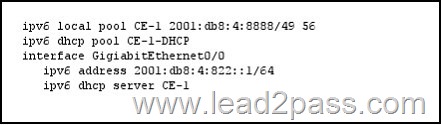
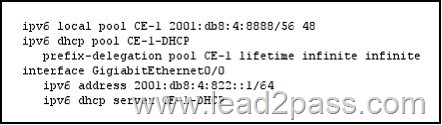
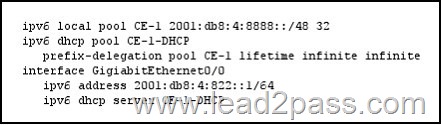
QUESTION 826
Refer to the exhibit. Which configuration can you implement on PE-1 to allow CE-1 to receive delegated IPv6 prefixes?
Answer: A
QUESTION 827
Which two statements about DHCP snooping are true? (Choose two.)
A. It is implemented on a per-VLAN basis.
B. It filters invalid DHCP messages.
C. The binding database logs trusted and untrusted hosts with leased IP addresses.
D. Interfaces are trusted by default.
E. It uses the LFIB to validate requests from untrusted hosts.
Answer: AB
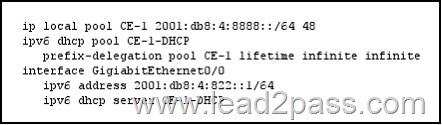
QUESTION 828
Refer to the exhibit. Which BGP feature allows R1 to instruct R2 which prefixes it is allowed to advertise to R1? 
A. route refresh
B. Prefix-Based Outbound Route Filtering
C. distribute lists
D. prefix lists
Answer: B
QUESTION 829
Which technology facilitates dynamic tunnel establishment in DMVPN?
A. CEF
B. mGRE
C. a dynamic routing protocol
D. NHRP
Answer: D
QUESTION 830
Which two statements about SNMP are true? (Choose two.)
A. SNMPv3 provides privacy and access control.
B. All SNMP versions use get, getNext, and getBulk operations.
C. SNMPv3 uses encrypted community strings.
D. SNMPv1 and SNMPv2c use plaintext community strings.
E. All SNMP versions support bulk retrieval and detailed error messages.
Answer: AB
QUESTION 831
Which two statements about route summarization are true? (Choose two.)
A. RIP, IGRP, and EIGRP can automatically summarize routing information at network address boundaries.
B. EIGRP can automatically summarize external routes.
C. The area range command can aggregate addresses on the ASBR.
D. The summary-address command under the router process configures manual summarization on RIPv2 devices.
E. The ip classless command enables classful protocols to select a default route to an unknown subnet on a network with other known subnets.
Answer: AE
QUESTION 832
Which two message types allow PIM snooping to forward multicast traffic? (Choose two.)
A. hello messages
B. leave messages
C. membership query messages
D. bidirectional PIM DF election messages
Answer: AD
QUESTION 833
Which feature of Cisco IOS XE Software allows for platform-independent code abstraction?
A. its security
B. Common Management Enabling Technology
C. the Linux-based environment
D. its modularity
Answer: D
QUESTION 834
Which statement about the VLAN database is true?
A. Manually deleting the vlan.dat file can cause inconsistency in the database.
B. Private VLAN information is stored in the database.
C. VLAN configurations 1 through 4096 are stored in the vlan.dat file.
D. The VLAN database is used only if the VTP domain name in the VLAN database matches the VTP domain name in the startup-config file.
Answer: A
QUESTION 835
In an STP domain, which two statements are true for a nonroot switch, when it receives a configuration BPDU from the root bridge with the TC bit set? (Choose two.)
A. It sets the MAC table aging time to max_age time.
B. It sets the MAC table aging time to forward_delay time.
C. It recalculates the STP topology upon receiving topology change notification from the root switch.
D. It does not recalculate the STP topology upon receiving topology change notification from the root switch.
Answer: BD
QUESTION 836
Which two statements about OSPF default route injection are true? (Choose two.)
A. The ABR requires manual configuration to send a default route into an NSSA area.
B. The ABR injects a default route into a Totally Stub Area.
C. In a stub area, the ASBR generates a summary LSA with link-state ID 0.0.0.0.
D. If the default route is missing from the routing table, the ASBR can use the default-information originate command to advertise the default into the OSPF domain.
E. By default, OSPF normal areas will generate default routes into the routing domain if a default route exists.
Answer: AB
QUESTION 837
Refer to the exhibit. While reviewing a log file on a router with this NTP configuration, you note that the log entries of the router display a different time than the NTP time. 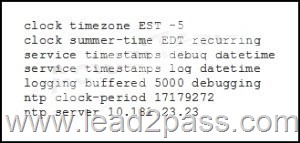
Which action can you take to correct the problem?
A. Add the localtime keyword to the service timestamps log datetime statement.
B. Add the msec keyword to the service timestamps log datetime statement.
C. Add the statement ntp broadcast to the NTP configuration of the neighboring router.
D. Configure the router to be the NTP master.
E. Remove the datetime keyword from the service timestamps log datetime statement.
Answer: A
QUESTION 838
What are the three variants of NTPv4? (Choose three.)
A. client/server
B. broadcast
C. symmetric
D. multicast
E. asymmetric
F. unicast
Answer: ABC
QUESTION 839
Which two options are mandatory components of a multiprotocol BGP VPN-IPv4 address? (Choose two.)
A. a system ID
B. a route target
C. a route distinguisher
D. an MPLS label
E. an area ID
F. an IPv4 address
Answer: CF
QUESTION 840
Which two statements about ERSPAN are true? (Choose two.)
A. It supports jumbo frames of up to 9202 bytes.
B. It adds a 50-byte header to copied Layer 2 Ethernet frames.
C. It supports packet fragmentation and reassembles the packets.
D. It adds a 4-byte header to copied Layer 2 Ethernet frames.
E. Source sessions on an individual switch can use different origin IP addresses.
Answer: AB
QUESTION 841
Which two statements about PBR route maps are true? (Choose two.)
A. They can use extended ACLs to identify traffic.
B. They can route unicast traffic without interface-level classification.
C. They can be applied to both ingress and egress traffic.
D. They can classify traffic based on prefix-lists.
E. They can set the metric and IP precedence bits.
Answer: AB
QUESTION 842
Which three events can cause a control plane to become overwhelmed? (Choose three.)
A. a worm attack
B. processing a stream of jumbo packets
C. a microburst
D. a configuration error
E. a reconvergence failure
F. a device-generated FTP session
Answer: ADE
QUESTION 843
Which three statements are true about unicast RPF? (Choose three.)
A. Unicast RPF requires CEF to be enabled.
B. Unicast RPF strict mode works better with multihomed networks.
C. Unicast RPF strict mode supports symmetric paths.
D. Unicast RPF strict mode supports asymmetric paths.
E. CEF is optional with Unicast RPF, but when CEF is enabled it provides better performance.
F. Unicast RPF loose mode is typically used with ISP networks.
Answer: ACF
QUESTION 844
What are three benefits of deploying NAT with ALG? (Choose three.)
A. the use of dynamic ephemeral ports through a firewall
B. the synchronization of translations between multiple streams of data
C. the use of deep packet inspection
D. the use of static ephemeral ports through a firewall
E. the conversion of session layer addresses from the application payload to outside global addresses
F. NAT traversal to support asymmetric data sessions
Answer: ABC
QUESTION 845
Which two statements about a network running MPLS VPN with IS-IS IGP are true? (Choose two.)
A. IS-IS traffic engineering uses wide metric TLV type 135 with an up/down bit to define a leaked route.
B. IS-IS traffic engineering uses wide metric TLV type 128 with an internal/external bit and an up/down bit to define a leaked route.
C. IS-IS traffic engineering uses wide metric TLV type 130 with an internal/external bit and an up/down bit to define a leaked route.
D. If the IS-IS up/down bit is set to 1, the leaked route originated in the L1 area.
E. The MPLS VPN IS-IS core is inherently protected against IP-based attacks.
Answer: AE
QUESTION 846
When VRF-Lite is configured without BGP support, which statement about the configuration of the route target and route distinguisher is true?
A. The configuration of the route target and route distinguisher is required.
B. The configuration of the route target and route distinguisher is not required.
C. The configuration of the route target is required and the configuration of the route distinguisher is not required.
D. The configuration of the route target is not required and the configuration of the route distinguisher is required.
Answer: D
QUESTION 847
How does MSTP provide backward compatibility with RSTP?
A. It uses the hop count variable as a TTL counter.
B. It transmits all spanning-tree information in one BPDU.
C. It supports up to 128 MSTI messages.
D. It encodes the MSTP-specific region information before the legacy RSTP BPDU.
Answer: D
QUESTION 848
Which standard feature can be exploited by an attacker to perform network reconnaissance?
A. IP-directed broadcast
B. maintenance operations ptotocol
C. ICMP redirects
D. source quench
Answer: C
QUESTION 849
How are the Cisco Express Forwarding table and the FIB related to each other?
A. The FIB is used to populate the Cisco Express Forwarding table.
B. The Cisco Express Forwarding table allows route lookups to be forwarded to the route processor for processing before they are
C. There can be only one FIB but multiple Cisco Express Forwarding tables on IOS devices.
D. Cisco Express Forwarding uses a FIB to make IP destination prefix-based switching decisions.
Answer: D
QUESTION 850
Which statement about the bgp soft-reconfig-backup command is true?
A. It requires BGP to store all inbound and outbound updates.
B. It overrides soft reconfiguration for devices that support inbound soft reconfiguration.
C. When the peer is unable to store updates, the updates are implemented immediately.
D. It provides soft reconfiguration capabilities for peers that are unable to support route refresh.
E. It provides outbound soft reconfiguration for peers.
Answer: D
Latest 400-101 questions and answers from Cisco Exam Center offered by Lead2pass for free share now! Read and remember all real questions answers, Guarantee pass 400-101 real test 100% or full money back!
400-101 new questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDU2RjeUlHTTZXb1U
2016 Cisco 400-101 exam dumps (All 1219 Q&As) from Lead2pass:
http://www.lead2pass.com/400-101.html [100% Exam Pass Guaranteed]vvvvvvvv