Free Download Cisco 350-001 VCE Test Engine Full Version Now (101-110)
QUESTION 101
Which two of these are used in the selection of a root bridge in a network utilizing Spanning Tree Protocol IEEE 802.1D? (Choose two.)
A. Designated Root Cost
B. bridge ID priority
C. max age
D. bridge ID MAC address
E. Designated Root Priority
F. forward delay
Answer: BD
Explanation:
The root bridge of the spanning tree is the bridge with the smallest (lowest) bridge ID. Each bridge has a unique identifier (ID) and a configurable priority number; the bridge ID contains both numbers. To compare two bridge IDs, the priority is compared first. If two bridges have equal priority, then the MAC addresses are compared. For example, if switches A (MAC=0200.0000.1111) and B (MAC=0200.0000.2222) both have a priority of 10, then switch A will be selected as the root bridge. If the network administrators would like switch B to become the root bridge, they must set its priority to be less than 10.
QUESTION 102
If a port configured with STP loop guard stops receiving BPDUs, the port will be put into which
state?
A. learning state
B. listening state
C. forwarding state
D. root-inconsistent state
Answer: D
Explanation:
STP Loop Guard
Feature Description
The STP loop guard feature provides additional protection against Layer 2 forwarding loops (STP loops). An STP loop is created when an STP blocking port in a redundant topology erroneously transitions to the forwarding state. This usually happens because one of the ports of a physically redundant topology (not necessarily the STP blocking port) no longer receives STP BPDUs. In its operation, STP relies on continuous reception or transmission of BPDUs based on the port role. The designated port transmits BPDUs, and the non-designated port receives BPDUs.
When one of the ports in a physically redundant topology no longer receives BPDUs, the STP conceives that the topology is loop free. Eventually, the blocking port from the alternate or backup port becomes designated and moves to a forwarding state. This situation creates a loop. The loop guard feature makes additional checks. If BPDUs are not received on a non-designated port, and loop guard is enabled, that port is moved into the STP loop-inconsistent blocking state, instead of the listening / learning / forwarding state. Without the loop guard feature, the port assumes the designated port role. The port moves to the STP forwarding state and creates a loop. When the loop guard blocks an inconsistent port, this message is logged:
CatOS%SPANTREE-2-LOOPGUARDBLOCK: No BPDUs were received on port 3/2 in vlan 3.
Moved to loop-inconsistent state.
Cisco IOS%SPANTREE-2-LOOPGUARD_BLOCK: Loop guard blocking port FastEthernet0/24 on VLAN0050.
Once the BPDU is received on a port in a loop-inconsistent STP state, the port transitions into another STP state. According to the received BPDU, this means that the recovery is automatic and intervention is not necessary. After recovery, this message is logged:
CatOS%SPANTREE-2-LOOPGUARDUNBLOCK: port 3/2 restored in vlan 3. Cisco IOS%SPANTREE-2-LOOPGUARD_UNBLOCK: Loop guard unblocking port FastEthernet0/24 on VLAN0050.
http://www.cisco.com/en/US/tech/tk389/tk621/technologies_tech_note09186a0080094640.shtml
QUESTION 103
What is the purpose of the STP PortFast BPDU guard feature?
A. enforce the placement of the root bridge in the network
B. ensure that a port is transitioned to a forwarding state quickly if a BPDU is received
C. enforce the borders of an STP domain
D. ensure that any BPDUs received are forwarded into the STP domain
Answer: C
Explanation:
STP configures meshed topology into a loop-free, tree-like topology. When the link on a bridge port goes up, STP calculation occurs on that port. The result of the calculation is the transition of the port into forwarding or blocking state. The result depends on the position of the port in the network and the STP parameters. This calculation and transition period usually takes about 30 to 50 seconds. At that time, no user data pass via the port. Some user applications can time out during the period. In order to allow immediate transition of the port into forwarding state, enable the STP PortFast feature.
PortFast immediately transitions the port into STP forwarding mode upon linkup. The port still participates in STP. So if the port is to be a part of the loop, the port eventually transitions into STP blocking mode.
As long as the port participates in STP, some device can assume the root bridge function and affect active STP topology. To assume the root bridge function, the device would be attached to the port and would run STP with a lower bridge priority than that of the current root bridge. If another device assumes the root bridge function in this way, it renders the network suboptimal. This is a simple form of a denial of service (DoS) attack on the network. The temporary introduction and subsequent removal of STP devices with low (0) bridge priority cause a permanent STP recalculation. The STP PortFast BPDU guard enhancement allows network designers to enforce the STP domain borders and keep the active topology predictable. The devices behind the ports that have STP PortFast enabled are not able to influence the STP topology. At the reception of BPDUs, the BPDU guard operation disables the port that has PortFast configured. The BPDU guard transitions the port into errdisable state, and a message appears on the console. This message is an example:
2000 May 12 15:13:32 %SPANTREE-2-RX_PORTFAST:Received BPDU on PortFast enable port.
Disabling 2/1
2000 May 12 15:13:32 %PAGP-5-PORTFROMSTP:Port 2/1 left bridge port 2/1
http://www.cisco.com/en/US/tech/tk389/tk621/technologies_tech_note09186a008009482f.shtml#topic1
QUESTION 104
Drag each definition on the left to the matching term on the right.
QUESTION 105
When STP UplinkFast is enabled on a switch utilizing the default bridge priority, what will the new bridge priority be changed to?
A. 8192
B. 16384
C. 49152
D. 65535
Answer: C
Explanation:
The STP UplinkFast is used to fast switchover to alternate ports when the root port fails. When STP UplinkFast is enabled on a switch utilizing the default bridge priority (32768), the new bridge priority will be changed to 49152. The reason for the priority being raised is to prevent the switch from becoming the root (recall that lower bridge priority is preferred). To enable UplinkFast feature, use the “set spantree uplinkfast enable” in privileged mode The set spantree uplinkfast enable command has the following results:
Changes the bridge priority to 49152 for all VLANs (allowed VLANs). Increases the path cost and portvlancost of all ports to a value greater than 3000. On detecting the failure of a root port, an instant cutover occurs to an alternate port selected by Spanning Tree Protocol (without using this feature, the network will need about 30 seconds to re- establish the connection.
http://www.cisco.com/en/US/tech/tk389/tk621/technologies_tech_note09186a0080094641.shtml
QUESTION 106
Which of these best describes the actions taken when a VTP message is received on a switch
configured with the VTP mode “transparent”?
A. VTP updates are ignored and forwarded out all ports.
B. VTP updates are ignored and forwarded out trunks only.
C. VTP updates are made to the VLAN database and are forwarded out trunks only.
D. VTP updates are ignored and are not forwarded.
Answer: B
Explanation:
You can configure a switch to operate in any one of these VTP modes:
Server–In VTP server mode, you can create, modify, and delete VLANs and specify other configuration parameters, such as VTP version and VTP pruning, for the entire VTP domain. VTP servers advertise their VLAN configuration to other switches in the same VTP domain and synchronize their VLAN configuration with other switches based on advertisements received over trunk links. VTP server is the default mode.
Client–VTP clients behave the same way as VTP servers, but you cannot create, change, or delete VLANs on a VTP client.
Transparent–VTP transparent switches do not participate in VTP. A VTP transparent switch does not advertise its VLAN configuration and does not synchronize its VLAN configuration based on received advertisements, but transparent switches do forward VTP advertisements that they receive out their trunk ports in VTP Version 2. Off (configurable only in CatOS switches)–In the three described modes, VTP advertisements are received and transmitted as soon as the switch enters the management domain state. In the VTP off mode, switches behave the same as in VTP transparent mode with the exception that VTP advertisements are not forwarded.
VTP V2
VTP V2 is not much different than VTP V1. The major difference is that VTP V2 introduces support for Token Ring VLANs. If you use Token Ring VLANs, you must enable VTP V2. Otherwise, there is no reason to use VTP V2. Changing the VTP version from 1 to 2 will not cause a switch to reload. VTP Password If you configure a password for VTP, you must configure the password on all switches in the VTP domain. The password must be the same password on all those switches. The VTP password that you configure is translated by algorithm into a 16-byte word (MD5 value) that is carried in all summary-advertisement VTP packets.
VTP Pruning
VTP ensures that all switches in the VTP domain are aware of all VLANs. However, there are occasions when VTP can create unnecessary traffic. All unknown unicasts and broadcasts in a VLAN are flooded over the entire VLAN. All switches in the network receive all broadcasts, even in situations in which few users are connected in that VLAN. VTP pruning is a feature that you use in order to eliminate or prune this unnecessary traffic.
http://www.cisco.com/en/US/tech/tk389/tk689/technologies_tech_note09186a0080094c52.shtml
QUESTION 107
Refer to the exhibit. In this network, R1 has been configured to advertise a summary route,
192.168.0.0/22, to R2. R2 has been configured to advertise a summary route, 192.168.0.0/21, to
R1. Both routers have been configured to remove the discard route (the route to null created when a summary route is configured) by setting the administrative distance of the discard route to 255.
What will happen if R1 receives a packet destined to 192.168.3.1?
A. The packet will loop between R1 and R2.
B. It is not possible to set the administrative distance on a summary to 255.
C. The packet will be forwarded to R2, where it will be routed to null0.
D. The packet will be dropped by R1, since there is no route to 192.168.3.1.
Answer: A
Explanation:
Indeed, when you change the administrative distance of the discard route to 255, this prevents the route to be installed in the routing table but this does not prevent the route to be advertised to the other peer!
QUESTION 108
Refer to the exhibit. In this network, R1 is configured not to perform autosummarization within
EIGRP. What routes will R3 learn from R2 through EIGRP?
A. 172.30.1.0/24 and 10.1.2.0/24; EIGRP only performs autosummarization at the edge between two
major networks.
B. 172.30.0.0/16 and 10.1.2.0/24; R2 will perform autosummarization, although R1 will not.
C. Since R2 is configured without autosummarization, it will not propagate the 172.30.1.0/24 route.
D. 172.30.0.0/8 and 10.0.0.0/8.
Answer: A
Explanation:
R1 is not configured for auto-summary but R2 is configured for auto-summary as auto-summary is enabled by default. Therefore although 172.30.1.0 is not summarized by R1 it will be summarized by R2 when R2 advertises this route to R3. However, both of R2’s interfaces are on the 10.x.x.x network and so is R3’s single interface. As auto summary is performed based on classful network boundaries R2 will advertise the classless network addresses of both interfaces to R3.
Auto-Summarization
EIGRP performs an auto-summarization each time it crosses a border between two different major networks.
For example, in Figure 13, Router Two advertises only the 10.0.0.0/8 network to Router One, because the interface Router Two uses to reach Router One is in a different major network.
http://www.cisco.com/en/US/tech/tk365/technologies_white_paper09186a0080094cb7.shtml#sum marizati on
QUESTION 109
The classic Spanning Tree Protocol (802.1D 1998) uses which sequence of variables to determine the best received BPDU?
A. 1) lowest root bridge id, 2) lowest sender bridge id, 3) lowest port id, 4) lowest root path cost
B. 1) lowest root path cost, 2) lowest root bridge id, 3) lowest sender bridge id, 4) lowest sender port id
C. 1) lowest root bridge id, 2) lowest sender bridge id, 3) lowest root path cost 4) lowest sender port id
D. 1) lowest root bridge id, 2) lowest root path cost, 3) lowest sender bridge id, 4) lowest sender port id
Answer: D
Explanation:
Configuration bridge protocol data units (BPDUs) are sent between switches for each port. Switches use a fourstep process to save a copy of the best BPDU seen on every port. When a port receives a better BPDU, it stops sending them. If the BPDUs stop arriving for 20 seconds (default), it begins sending them again.
Step 1 Lowest Root Bridge ID (BID)
Step 2 Lowest Path cost to Root Bridge
Step 3 Lowest Sender BID
Step 4 Lowest Port ID
Cisco General Networking Theory Quick Reference Sheets
QUESTION 110
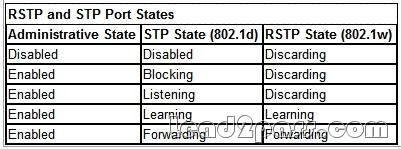
Which three port states are used by RSTP 802.1w? (Choose three.)
A. Listening
B. Learning
C. Forwarding
D. Blocking
E. Discarding
F. Disabled
Answer: BCE
Explanation:
If you want to pass Cisco 350-001 exam successfully, donot missing to read latest lead2pass Cisco 350-001 dumps.
If you can master all lead2pass questions you will able to pass 100% guaranteed.