Free Download Cisco 350-001 VCE Test Engine Full Version Now (11-20)
QUESTION 11
How is RPF used in multicast routing?
A. to prevent multicast packets from looping
B. to prevent PIM packets from looping
C. to instruct PIM where to send a (*,G) or (S,G) join message
D. to prevent multicast packets from looping and to instruct PIM where to send a (*,G) or (S,G) join message
Answer: D
QUESTION 12
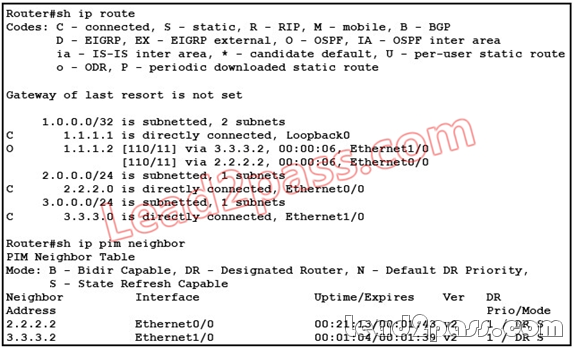
Refer to the exhibit. What does the incoming interface of the above (*,G) entry indicate?
A. the interface closest to the source, according to the unicast routing table
B. the interface where an IGMP join has been received
C. the interface with the highest IP address
D. the last interface to hear a PIM (*,G) join
E. the interface closest to the RP, according to the unicast routing table
Answer: E
Explanation:
Source Trees
A source tree is the simplest form of distribution tree. The source host of the multicast traffic is located at the root of the tree, and the receivers are located at the ends of the branches. Multicast traffic travels from the source host down the tree toward the receivers. The forwarding decision on which interface a multicast packet should be transmitted out is based on the multicast forwarding table. This table consists of a series of multicast state entries that are cached in the router. State entries for a source tree use the notation (S, G) pronounced S comma G. The letters represents the IP address of the source, and G represents the group address.
Shared Trees
Shared trees differ from source trees in that the root of the tree is a common point somewhere in the network.
This common point is referred to as the rendezvous point (RP). The RP is the point at which receivers join to learn of active sources. Multicast sources must transmit their traffic to the RP. When receivers join a multicast group on a shared tree, the root of the tree is always the RP, and multicast traffic is transmitted from the RP down toward the receivers. Therefore, the RP acts as a go-between for the sources and receivers. An RP can be the root for all multicast groups in the network, or different ranges of multicast groups can be associated with different RPs. Multicast forwarding entries for a shared tree use the notation (*, G), which is pronounced star comma G. This is because all sources for a particular group share the same tree. (The multicast groups go to the same RP.)
Therefore, the * or wildcard represents all sources.
Additional Information from Microsoft
Multicast traffic from source 162.10.4.1 (for example) uses the RPT, meaning the source sends it to the RP rather than to the multicast group (the router would denote this by having a (*, G) entry rather than a (S, G) entry). Before sending this traffic, Router 1 checks its unicast routing table to see if packets from the RP are arriving on the correct interface. In this case they are, because they arrive on interface I1, and the packets are forwarded.
http://technet.microsoft.com/en-us/library/bb742462.aspx
QUESTION 13
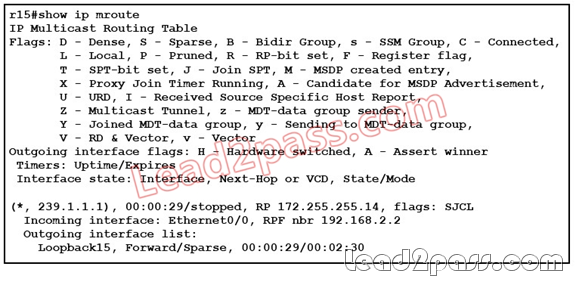
Refer to the exhibit. Which interface(s) will show ip rpf 1.1.1.2 indicate as RPF interface(s)?
A. Ethernet 1/0
B. Ethernet 0/0
C. Both Ethernet 0/0 and Ethernet 1/0
D. RPF will fail
Answer: A
Explanation:
When troubleshooting multicast routing, the primary concern is the source address. Multicast has a concept of Reverse Path Forwarding check (RPF check). When a multicast packet arrives on an interface, the RPF process checks to ensure that this incoming interface is the outgoing interface used by unicast routing to reach the source of the multicast packet. This RPF check process prevents loops. Multicast routing does not forward a packet unless the source of the packet passes a reverse path forwarding (RPF) check. Once a packet passes this RPF check, multicast routing forwards the packet based only upon the destination address.
http://www.cisco.com/en/US/tech/tk828/technologies_tech_note09186a0080094b55.shtml
QUESTION 14
Apart from interdomain multicast routing, what else is MSDP used for?
A. Source Specific Multicast and IGMPv2
B. Announcing multicast sources to BGP speakers
C. Anycast RP
D. Intradomain multicast routing
Answer: C
Explanation:
http://www.cisco.com/en/US/docs/ios/12_2/ip/configuration/guide/1cfmsdp_ps1835_TSD_Products_Configuration_Guide_Chapter.html
QUESTION 15
Which IGMPv2 message contains a non-zero “Max Response Time”?
A. Membership Query
B. Membership Report
C. Membership Delay
D. Backward Compatible IGMPv1 Report Message
Answer: A
Explanation:
The Max Response Time field is used only in Membership Query messages. It specifies the maximum allowed time before sending a responding report in units of 1/10 second. In all other messages, it is set to zero by the sender and ignored by receivers.
QUESTION 16
Refer to the exhibit. Which IGMPv2 message is displayed in the output of the packet capture?
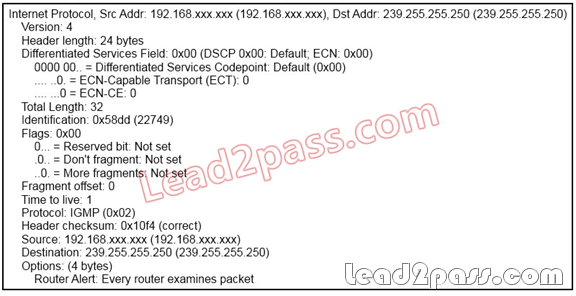
A. General Query
B. Membership Report
C. Membership Query
D. Membership Delay
Answer: B
Explanation:
http://wiki.wireshark.org/IGMP
QUESTION 17
What is Phantom RP used for?
A. it is used for load balancing in bidirectional PIM
B. it is used for redundancy in bidirectional PIM
C. it is used for redundancy in PIM-SM
D. it is used for load balancing in PIM-SM
Answer: B
Explanation:
Phantom RP
In Bidirectional PIM (Bidir-PIM), the RP does not have an actual protocol function. The RP acts as a routing vector in which all the traffic converges. The RP can be configured as an address that is not assigned to any particular device called a Phantom RP. This means that the RP address does not need to reside on a physical router interface, but can just be an address in a subnet. The RP can also be a physical router, but it is not necessary.
http://www.cisco.com/en/US/prod/collateral/iosswrel/ps6537/ps6552/whitepaper_c11-508498.html
QUESTION 18
Which three statements are true about TACACS+? (Choose three.)
A. It is a Cisco proprietary protocol.
B. It runs on TCP port 59.
C. Authentication and authorization are done at different stages.
D. TACACS+ encrypts the entire body of the packet, but leaves a standard TACACS+ header.
E. It is an industry standard protocol.
F. TACACS+ encrypts both the entire body of the packet and the TACACS+ header.
Answer: ACD
Explanation:
TACACS+ utilizes TCP port 49. It consists of three separate protocols, which can be implemented on separate servers.[1]
TACACS+ offers multiprotocol support, such as IP and AppleTalk. Normal operation fully encrypts the body of the packet for more secure communications. It is a Cisco proprietary enhancement to the original TACACS protocol.
http://en.wikipedia.org/wiki/TACACS%2B
QUESTION 19
Refer to the exhibit. Which two statements are correct? (Choose two.)
A. The hexadecimal value of the number of packets that hit the access list is 0x723E6E12.
B. The access list has logging enabled.
C. The packet was discarded.
D. The command ip access-list logging hash-generation is enabled.
E. The Telnet connection is successfully set up.
Answer: BD
Explanation:
http://www.packetu.com/2009/07/31/ccie-security-quick-tips/
QUESTION 20
Refer to the exhibit. Which statement is correct?
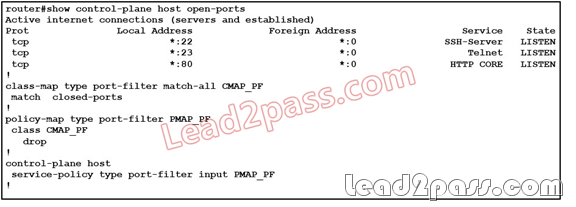
A. This configuration is not valid.
B. Control Plane Policing is configured; however you cannot determine on which interface it is
configured.
C. NTP is not configured on the router.
D. Telnet traffic will be dropped.
Answer: C
Explanation:
Display the current connection table for the router. For example, for IOS routers, type “show control-plane host open-ports” Press “Enter.” The router will display a table with one line for each currently open connection. The fourth column from the left is labeled “Service;” the entries under
that column correspond to the protocols currently in use. The current TCP traffic corresponds exactly to the table entries that have “TCP” under the fourth column.
…go to http://www.lead2pass.com/350-001.html to download the full version Q&As.