Free Download Cisco 350-001 VCE Test Engine Full Version Now (71-80)
QUESTION 71
While you are troubleshooting network performance issues, you notice that a switch is periodically flooding all unicast traffic. Further investigation reveals that periodically the switch is also having spikes in CPU utilization, causing the MAC address table to be flushed and relearned. What is the most likely cause of this issue?
A. a routing protocol that is flooding updates
B. a flapping port that is generating BPDUs with the TCN bit set
C. STP is not running on the switch
D. a user that is downloading the output of the show-tech command
E. a corrupted switch CAM table
Answer: B
Explanation:
Spanning-Tree Protocol Topology Changes
Another common issue caused by flooding is Spanning-Tree Protocol (STP) Topology Change Notification (TCN). TCN is designed to correct forwarding tables after the forwarding topology has changed. This is necessary to avoid a connectivity outage, as after a topology change some destinations previously accessible via particular ports might become accessible via different ports. TCN operates by shortening the forwarding table aging time, such that if the address is not relearned, it will age out and flooding will occur. TCNs are triggered by a port that is transitioning to or from the forwarding state. After the TCN, even if the particular destination MAC address has aged out, flooding should not happen for long in most cases since the address will be relearned. The issue might arise when TCNs are occurring repeatedly with short intervals. The switches will constantly be fast-aging their forwarding tables so flooding will be nearly constant. Normally, a TCN is rare in a well-configured network. When the port on a switch goes up or down, there is eventually a TCN once the STP state of the port is changing to or from forwarding. When the port is flapping, repetitive TCNs and flooding occurs.
Ports with the STP portfast feature enabled will not cause TCNs when going to or from the forwarding state. Configuration of portfast on all end-device ports (such as printers, PCs, servers, and so on) should limit TCNs to a low amount. Refer to this document for more information on TCNs:
Understanding Spanning-Tree Protocol Topology Changes Note: In MSFC IOS, there is an optimization that will trigger VLAN interfaces to repopulate their ARP tables when there is a TCN in the respective VLAN. This limits flooding in case of TCNs, as there will be an ARP broadcast and the host MAC address will be relearned as the hosts reply to ARP.
http://www.cisco.com/en/US/products/hw/switches/ps700/products_tech_note09186a00801d0808.shtml
QUESTION 72
Your network is suffering from regular outages. After troubleshooting, you learn that the transmit lead of a fiber uplink was damaged. Which two features can prevent the same issues in the
future? (Choose two.)
A. root guard
B. loop guard
C. BPDU guard
D. UDLD
E. BPDU skew detection
Answer: BD
Explanation:
STP Loop Guard
The STP loop guard feature provides additional protection against Layer 2 forwarding loops (STP loops). An STP loop is created when an STP blocking port in a redundant topology erroneously transitions to the forwarding state. This usually happens because one of the ports of a physically redundant topology (not necessarily the STP blocking port) no longer receives STP BPDUs. In its operation, STP relies on continuous reception or transmission of BPDUs based on the port role. The designated port transmits BPDUs, and the non-designated port receives BPDUs. When one of the ports in a physically redundant topology no longer receives BPDUs, the STP conceives that the topology is loop free. Eventually, the blocking port from the alternate or backup port becomes designated and moves to a forwarding state. This situation creates a loop. The loop guard feature makes additional checks. If BPDUs are not received on a non-designated port, and loop guard is enabled, that port is moved into the STP loop-inconsistent blocking state, instead of the listening / learning / forwarding state. Without the loop guard feature, the port assumes the designated port role. The port moves to the STP forwarding state and creates a loop.
Loop Guard versus UDLD
Loop guard and Unidirectional Link Detection (UDLD) functionality overlap, partly in the sense that both protect against STP failures caused by unidirectional links. However, these two features differ in functionality and how they approach the problem. This table describes loop guard and UDLD functionality:
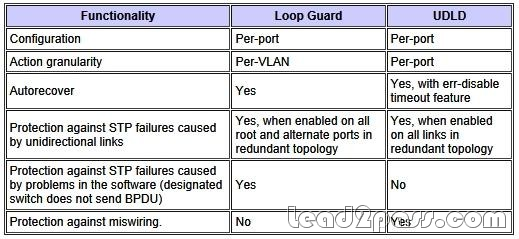
Based on the various design considerations, you can choose either UDLD or the loop guard feature. In regards to STP, the most noticeable difference between the two features is the absence of protection in UDLD against STP failures caused by problems in software. As a result, the designated switch does not send BPDUs.
However, this type of failure is (by an order of magnitude) more rare than failures caused by unidirectional links. In return, UDLD might be more flexible in the case of unidirectional links on EtherChannel. In this case, UDLD disables only failed links, and the channel should remain functional with the links that remain. In such a failure, the loop guard puts it into loop-inconsistent state in order to block the whole channel.
Additionally, loop guard does not work on shared links or in situations where the link has been unidirectional since the link-up. In the last case, the port never receives BPDU and becomes designated. Because this behavior could be normal, this particular case is not covered by loop guard.
UDLD provides protection against such a scenario.
As described, the highest level of protection is provided when you enable UDLD and loop guard.
http://www.cisco.com/en/US/tech/tk389/tk621/technologies_tech_note09186a0080094640.shtml#loop_guard_vs_uld
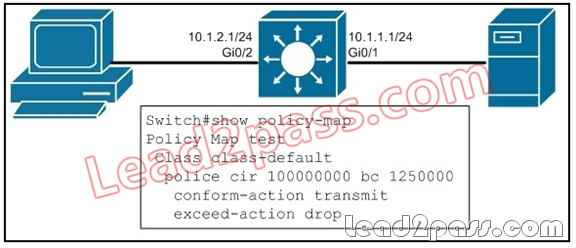
QUESTION 73
Refer to the exhibit. You are trying to police down to 100 Mb/s. While testing, you notice that you rarely exceed 70-80 Mb/s. What do you need to change in your MQC configuration to allow for 100 Mb/s speeds?
A. Change the CIR value from 100 Mb/s to 200 Mb/s.
B. Change the Bc value to allow for a large enough burst.
C. Change the QoS queue from default to priority.
D. Change the exceed-action to transmit.
Answer: B
Explanation:
Burst size–Also called the Committed Burst (Bc) size, it specifies in bits (or bytes) per burst how much traffic can be sent within a given unit of time to not create scheduling concerns. (For a shaper, such as GTS, it specifies bits per burst; for a policer, such as CAR, it specifies bytes per burst.)
QUESTION 74
Which feature would prevent guest users from gaining network access by unplugging an IP phone
and connecting a laptop computer?
A. IPSec VPN
B. SSL VPN
C. port security
D. port security with statically configured MAC addresses
E. private VLANs
Answer: D
Explanation:
http://www.cisco.com/en/US/docs/switches/lan/catalyst6500/ios/12.2SX/configuration/guide/port_sec.html#wp1061587
QUESTION 7
After applying a new ACL on a device, its CPU utilization rose significantly and many messages
starting with “%SEC-6-IPACCESSLOG” appeared on the Syslog server.
What can be done to resolve this situation?
A. Increase memory allocation for ACLs.
B. Remove all entries from the ACL and use a single permit ip any any statement.
C. Remove the log keyword from each ACL entry.
D. Reboot the device after the ACL has been applied.
Answer: C
Explanation:
http://www.networksa.org/?p=347
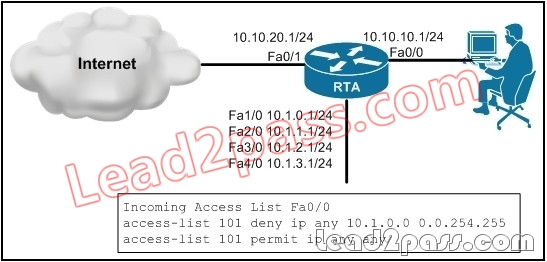
QUESTION 76
Refer to the exhibit. Clients that are connected to Fa0/0 of RTA are only allowed to connect to the Internet and networks, but not the networks on Fa1/0, Fa2/0, Fa3/0 and Fa4/0. To achieve this, you have configured an ACL on RTA and applied it on the incoming direction of interface Fa0/0.
After you apply this ACL, you learn that some of these networks are still accessible for clients that are connected to the 10.10.10.0/24
network. What is the correct ACL configuration to solve this
issue?
A. access-list 101 deny ip any 10.1.0.0 0.0.1.255
access-list 101 permit ip any any
B. access-list 101 permit ip any 10.1.0.0 0.0.1.255
access-list 101 deny ip any any
C. access-list 101 deny ip any 10.1.0.0 0.0.252.255
access-list 101 permit ip any any
D. access-list 101 deny ip any 10.1.0.0 0.0.3.255
access-list 101 permit ip any any
Answer: D
Explanation:
Access-lists use a wild card mask which is incorrectly configured in the above example Reference
http://www.cisco.com/en/US/products/sw/secursw/ps1018/products_tech_note09186a00800a5b9a.shtml
QUESTION 77
You are the network administrator of a medium-sized company, and users are complaining that
they cannot send emails to some organizations. During your troubleshooting, you notice that your DNS MX record is blacklisted by several public blacklist filters. After clearing these listings for your IP address, and assuming that your email server has the right virus protection in place, what are two possible solutions to prevent this from happening in the future? (Choose two.)
A. Change your Internet provider.
B. Change your public IP address.
C. Allow the email server to send traffic only to TCP port 25.
D. Put your email server in a DMZ.
E. Use a separate public IP address for your email server only.
Answer: CE
Explanation:
http://www.parkansky.com/tutorials/dmz.htm
QUESTION 78
Refer to the exhibit. What can be done to remove the summary routes to Null0 on R3?
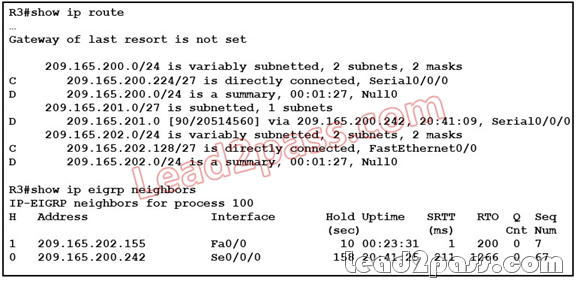
A. Configure the EIGRP routing subcommand no auto-summary on 209.165.202.155.
B. Configure the EIGRP routing subcommand no auto-summary on 209.165.202.24.
C. Configure the EIGRP routing subcommand no auto-summary on both 209.165.202.155 and
209.165.202.242.
D. Configure the EIGRP routing subcommand no auto-summary on R3.
Answer: D
Explanation:
Disabling automatic summarization will remove the Null0 summary route and allow EIGRP to look for a supernet or default route when an EIGRP child route does not match a destination packet.
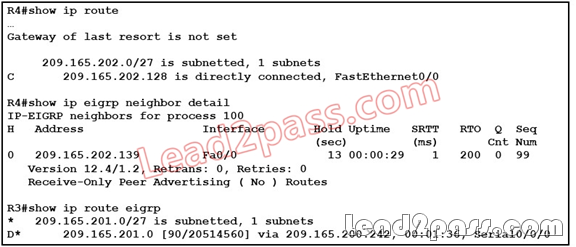
QUESTION 79
Refer to the exhibit. R4 is configured as a receive-only EIGRP stub, and is adjacent with 209.165.202.139 (R3).
However, R4 is not learning about network 209.165.201.0/27 from R3. What could be the cause
of this issue?
A. R4 should learn this route from 209.165.200.242, and not from R3.
B. R3 is configured as a receive-only EIGRP stub.
C. R3 and R4 may be using different EIGRP process numbers.
D. R3 and R4 are asymmetrically adjacent neighbors.
Answer: B
Explanation:
Configuring EIGRP Stub Routing
To configure a remote or spoke router for EIGRP stub routing, use the following commands beginning in router configuration mode:
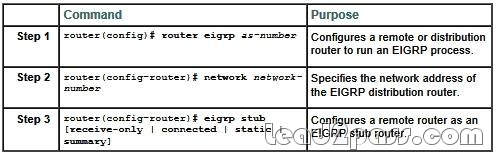
http://www.cisco.com/en/US/docs/ios/12_0s/feature/guide/eigrpstb.html
QUESTION 80
Refer to the exhibit. R4 is a remote office router that is running EIGRP; the decision has been made to change EIGRP to use static EIGRP adjacencies. However, once the configuration change was applied, the adjacency between R4 and 209.165.202.139 (HQ) seems to disappear. What could be the cause of this issue?
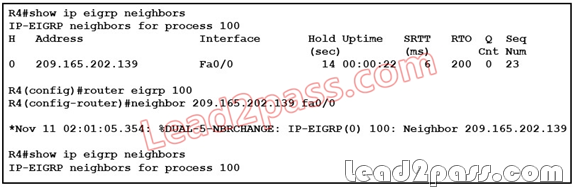
A. Static EIGRP neighbor configuration is symmetric; it causes the interface to stop processing
inbound multicast packets and stop sending multicast packets.
B. Static EIGRP neighbors are not displayed with the show ip eigrp neighbors command.
C. A distance (internal 90 or external 170) must also be configured for the static neighbor.
D. The neighbor 209.165.202.139 should be changed to run under EIGRP autonomous system 0.
Answer: A
Explanation:
As you can see that static EIGRP neighbor configuration is symmetric. This causes the interface to halt processing inbound packets and stop sending multicast packets.
…go to http://www.lead2pass.com/350-001.html to download the full version Q&As.