[Full Version] Free 400-251 Exam Dumps With PDF And VCE Download (241-260)
2017 February Cisco Official New Released 400-251 Dumps in Lead2pass.com!
100% Free Download! 100% Pass Guaranteed!
In recent years, many people choose to take Cisco 400-251 certification exam which can make you get the Cisco certificate and that is the passport to get a better job and get promotions. How to prepare for Cisco 400-251 exam and get the certificate? Please refer to Cisco 400-251 exam questions and answers on Lead2pass.
Following questions and answers are all new published by Cisco Official Exam Center: http://www.lead2pass.com/400-251.html
QUESTION 241
Which Cisco product solution is designed for workload mobility between public-public and private-public clouds?
A. Cisco Cloud Orchestrator
B. Cisco Unified Cloud
C. Cisco Intercloud Fabric
D. Cisco Metapod
Answer: C
QUESTION 242
Refer to the exhibit. What protocol format is illustrated?
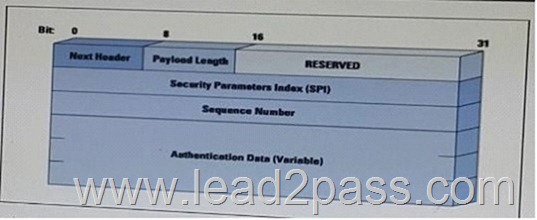
A. GR
B. AH
C. ESP
D. IP
Answer: B
QUESTION 243
What are two features that help to mitigate man-in-the-middle attacks?(Choose two)
A. dynamic ARP inspection
B. ARP sniffing on specific ports
C. destination MAC ACLs
D. ARP spoofing
E. DHCP snooping
Answer: AE
QUESTION 244
What is the purpose of the vulnerability risk method for assessing risk?
A. It directs the actions an organization can take in response to a reported vulnerability
B. It evaluates the effectiveness and appropriateness of an organization’s current risk management activities
C. It directs the actions an organization can take to ensure perimeter security
D. It prevents and protects against security vulnerabilities in an organization
E. It establishes a security team to perform forensic examinations of known attacks
Answer: C
QUESTION 245
Which three IP resources is the IANA responsible? (Choose three.)
A. IP address allocation
B. detection of spoofed address
C. criminal prosecution of hackers
D. autonomous system number allocation
E. root zone management in DNS
F. BGP protocol vulnerabilities
Answer: ADE
QUESTION 246
Which Statement about remote procedure calls is true?
A. They support synchronous and asynchronous requests.
B. They can emulate different hardware specifications on a single platform.
C. They support optimized data replication among multiple machines.
D. They use a special assembly instruction set to process remote code without conflicting with other remote processes.
E. They can be invoked by the client and the server.
Answer: D
QUESTION 247
You have configured an authenticator switch in access mode on a network configured with NEAT.
What RADIUS attribute must the ISE sever return to change the switch’s port mode to trunk?
A. device-traffic-class=switch
B. device-traffic-class=trunk
C. Framed-protocol=1
D. EAP-message=switch
E. Acct-Authentic=RADIUS
F. Authenticate=Administrative
Answer: A
QUESTION 248
Which statement about ISO/IEC 27001 is true?
A. ISO/IEC 27001 is only intended to report security breaches to the management authority.
B. ISO/IEC 27001 was reviewed by the International Organization for Standardization.
C. ISO/IEC 27001 is intend to bring information security under management control.
D. ISO/IEC 27001 was reviewed by the International Electrotechnical Commission.
E. ISO/IEC 27001 was published by ISO/IEC
Answer: C
QUESTION 249
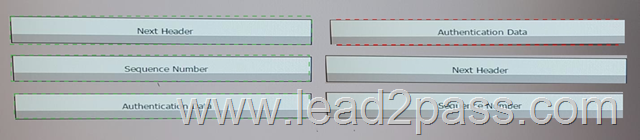
Drag and Drop Question
Drag and drop ESP header field on the left to the appropriate field length on the right.

Answer:
QUESTION 250
Which object table contains information about the clients know to the server in Cisco NHRP MIB implementaion?
A. NHRP Server NHC Table
B. NHRP Client Statistics Table
C. NHRP Cache Table
D. NHRP Purge Request Table
Answer: A
QUESTION 251
Which three Cisco attributes for LDAP authorization are supported on the ASA? (Choose three)
A. L2TP-Encryption
B. Web-VPN-ACL-Filters
C. IPsec-Client-Firewall-Filter-Name
D. Authenticated-User-Idle-Timeout
E. IPsec-Default-Domain
F. Authorization-Type
Answer: BDE
QUESTION 252
Which two options are system requirements for single sign-on on Cisco Unified Communications Manager? (Choose two)
A. OpenAM must be deployed in a different domain Microsoft Active Directory.
B. All participating entities must have their clocks synchronized.
C. The local user profile on Cisco Unified Communications must be disabled.
D. IWA and Kerberos authentication must be configured in the Windows domain.
E. Microsoft Active Directory must be deployed in a domain-based configuration.
Answer: BE
QUESTION 253
Which of the following statement is true about the ARP attack?
A. Attackers sends the ARP request with the MAC address and IP address of a legitimate resource in the network.
B. Attackers sends the ARP request with the MAC address and IP address of its own.
C. ARP spoofing does not facilitate man-in-the middle attack of the attackers.
D. Attackers sends the ARP request with its own MAC address and IP address of a legitimate resource in the network.
Answer: D
QUESTION 254
During a DoS attacks all of the data is lost from a user’s laptop and the user must now rebuild the system.
Which tool can the user use to extract the outlook PST file from the Microsoft server database?
A. Eseutil. exe
B. NTabackup.cex
C. Exmerge.exe
D. Ost2st.exe
Answer: C
QUESTION 255
A Cisco Easy VPN software client is unable to access its local LAN devices once the VPN tunnel is established.
What is the best way to solve this issue?
A. The IP address that is assigned by the Cisco Easy VPN Server to the client must be on the same network as the local LAN of the client.
B. The Cisco Easy VPN Server should apply split-tunnel-policy excludespecified with a split-tunnel-list containing the local LAN addresses that are relevant to the client.
C. The Cisco Easy VPN Server must push down an interface ACL that permits the traffic to the local LAN from the client.
D. The Cisco Easy VPN Server should apply a split-tunnel-policy tunnelall policy to the client.
E. The Cisco Easy VPN client machine needs to have multiple NICs to support this.
Answer:
QUESTION 256
Which two statements about IKEv2 are true? (Choose two)
A. It uses EAP authentication
B. It uses X.509 certificates for authentication
C. The profile is a collection of transforms used to negotiate IKE SAs
D. It supports DPD and Nat-T by default
E. The profile contains a repository of symmetric and asymmetric preshared keys
F. At minimum, a complete proposal requires one encryption algorithm and one integrity algorithm
Answer: EF
QUESTION 257
Which two OSPF network types support the concept of a designated router? (Choose two.)
A. broadcast
B. NBMA
C. point-to-multipoint
D. point-to-multipoint nonbroadcast
E. loopback
Answer: AB
QUESTION 258
Given the IPv4 address 10.10.100.16, which two address are valid IPv4-compatible IPv6 addresses? (Choose twoChoose two)
A. 0:0:0:0:0:10:10:100:16
B. 0:0:10:10:10:16:0:0:0
C. 0:0:10:10:100:16:0:0:0
D. ::10:10:100:16
E. :::A:A:64:10
Answer: AD
QUESTION 259
What technology can you implement on your network to allow IPv4-dependent applications to work with IPv6- capable application?
A. NAT 6to4
B. DS-lite
C. NAT-PT
D. ISATAP
E. NAT64
Answer: E
QUESTION 260
Which three fields are part of the AH header? (Choose three)
A. Destination address
B. Protocol ID
C. Packet ICV
D. SPI identifying SA
E. Next header
F. Application port
G. Source address
Answer: CDE
Lead2pass is a good website that provides all candidates with the latest IT certification exam materials. Lead2pass will provide you with the exam questions and verified answers that reflect the actual exam. The Cisco 400-251 exam dumps are developed by experienced IT professionals. 99.9% of hit rate. Guarantee you success in your 400-251 exam with our exam materials.
400-251 new questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDbkNSWnpMam9TWWM
2017 Cisco 400-251 exam dumps (All 336 Q&As) from Lead2pass:
http://www.lead2pass.com/400-251.html [100% Exam Pass Guaranteed]