[January 2018] Free Sharing Of Cisco 400-251 Brain Dumps From Lead2pass 727q
Free Sharing Of Updated 400-251 VCE And PDF Dumps From Lead2pass:
https://www.lead2pass.com/400-251.html
QUESTION 1
According to OWASP guidelines, what is the recommended method to prevent cross-site request forgery?
A. Allow only POST requests.
B. Mark all cookies as HTTP only.
C. Use per-session challenge tokens in links within your web application.
D. Always use the “secure” attribute for cookies.
E. Require strong passwords.
Answer: C
QUESTION 2
What is the maximum pattern length supported by FPM searches within a packet?
A. 256 bytes
B. 128 bytes
C. 512 bytes
D. 1500 bytes
Answer: A
QUESTION 3
Which two statements about role-based access control are true?(Choose two)
A. Server profile administrators have read and write access to all system logs by default.
B. If the same user name is used for a local user account and a remote user account, the roles defined in the remote user account override the local user account.
C. A view is created on the Cisco IOS device to leverage role-based access controls.
D. Network administrators have read and write access to all system logs by default.
E. The user profile on an AAA server is configured with the roles that grant user privileges.
Answer: CE
QUESTION 4
Which three global correlation feature can be enabled from cisco IPD device manager (Cisco IDM)? (Choose three)
A. Network Reputation
B. Global Data Interaction
C. Signature Correlation
D. Reputation Filtering
E. Global Correlation Inspection
F. Data Contribution
G. Reputation Assignment
Answer: ADE
Explanation:
http://www.cisco.com/c/en/us/td/docs/security/ips/7-0/configuration/guide/idm/idmguide7/idm_collaboration.html
QUESTION 5
According to RFC 4890, which three message must be dropped at the transit firewall/router?(Choose three.)
A. Router Renumbering (Type 138)
B. Node Information Query (Type 139)
C. Router Solicitation (Type 133)
D. Node information Response (Type 140)
E. Router Advertisement (Type 134)
F. Neighbor Solicitation (Type 135)
Answer: ABD
QUESTION 6
What is the effect of the following command on Cisco IOS router?
ip dns spoofing 1.1.1.1
A. The router will respond to the DNS query with its highest loopback address configured
B. The router will respond to the DNS query with 1.1.1.1 if the query id for its own hostname
C. The router will respond to the DNS query with the IP address of its incoming interface for any hostname query
D. The router will respond to the DNS query with the IP address of its incoming interface for its own hostname
Answer: D
QUESTION 7
Which two options are differences between automation and orchestration? (Choose two)
A. Automation is to be used to replace human intervention
B. Automation is focused on automating a single or multiple tasks
C. Orchestration is focused on an end-to-end process or workflow
D. Orchestration is focused on multiple technologies to be integrated together
E. Automation is an IT workflow composed of tasks, and Orchestration is a technical task
Answer: BC
QUESTION 8
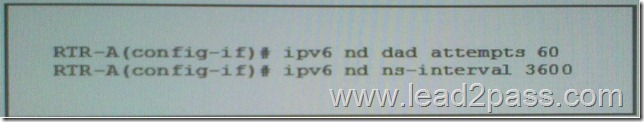
Refer to the exhibit. What is the effect of the given configuration?
A. It sets the duplicate address detection interval to 60 second and sets the IPv6 neighbor reachable time to 3600 milliseconds.
B. It sets the number of neighbor solicitation massages to 60 and sets the retransmission interval to
3600 milliseconds.
C. It sets the number of duplicate address detection attempts to 60 and sets the duplicate address detection interval to 3600 millisecond.
D. It sets the number of neighbor solicitation massage to 60 and set the duplicate address detection interval to 3600 second.
E. It sets the duplicate address detection interval to 60 second and set the IPv6 neighbor solicitation interval to 3600 millisecond.
Answer: B
Explanation:
http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/ipv6/command/ipv6-cr-book/ipv6-i3.html#wp3064574124
http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/ipv6/command/ipv6-cr-book/ipv6-i3.html#wp3676879817
QUESTION 9
What are two characteristics of RPL, used in loT environments? (Choose two)
A. It is an Exterior Gateway Protocol
B. It is a Interior Gateway Protocol
C. It is a hybrid protocol
D. It is link-state protocol
E. It is a distance-vector protocol
Answer: BE
QUESTION 10
In a Cisco ASA multiple-context mode of operation configuration, what three session types are resource-limited by default when their context is a member of the default class?(choose three).
A. Telnet sessions
B. ASDM sessions
C. IPSec sessions
D. SSH sessions
E. TCP sessions
F. SSL VPN sessions
Answer: ABD
400-251 dumps full version (PDF&VCE): https://www.lead2pass.com/400-251.html
Large amount of free 400-251 exam questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDU1JrNmttR1dfUm8