[Lead2pass New] Lead2pass Fortinet NSE4 Latest Exam Dumps Download (226-250)
Lead2pass 2017 November New Fortinet NSE4 Exam Dumps!
100% Free Download! 100% Pass Guaranteed!
Fortinet NSE4 is omnipresent all around the world, and the business and software solutions provided by them are being embraced by almost all the companies. They have helped in driving thousands of companies on the sure-shot path of success. Comprehensive knowledge of Fortinet NSE4 products is considered a very important qualification, and the professionals certified by them are highly valued in all organizations.
Following questions and answers are all new published by Fortinet Official Exam Center: https://www.lead2pass.com/nse4.html
QUESTION 226
Which of the following statements are correct regarding virtual domains (VDOMs)? (Select all that apply.)
A. VDOMs divide a single FortiGate unit into two or more virtual units that function as multiple, independent units.
B. A management VDOM handles SNMP, logging, alert email, and FDN-based updates.
C. VDOMs share firmware versions, as well as antivirus and IPS databases.
D. Only administrative users with a ‘super_admin’ profile will be able to enter multiple VDOMs to make configuration changes.
Answer: ABC
QUESTION 227
Which of the following statements are TRUE for Port Pairing and Forwarding Domains? (Select all that apply.)
A. They both create separate broadcast domains.
B. Port Pairing works only for physical interfaces.
C. Forwarding Domains only apply to virtual interfaces.
D. They may contain physical and/or virtual interfaces.
E. They are only available in high-end models.
Answer: AD
QUESTION 228
Examine the Exhibits shown below, then answer the question that follows.
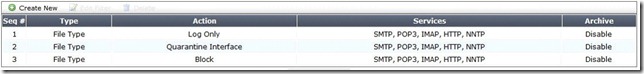
Review the following DLP Sensor (Exhibit 1):
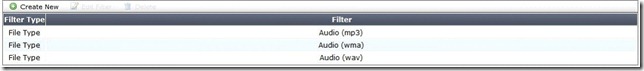
Review the following File Filter list for rule #1 (Exhibit 2):
Review the following File Filter list for rule #2 (Exhibit 3):
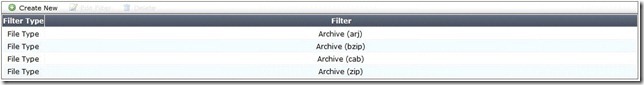
Review the following File Filter list for rule #3 (Exhibit 4):
An MP3 file is renamed to `workbook.exe’ and put into a ZIP archive. It is then sent through the FortiGate device over HTTP. It is intercepted and processed by the configuration shown in the above Exhibits 1-4.
Assuming the file is not too large for the File scanning threshold, what action will the FortiGate unit take?
A. The file will be detected by rule #1 as an `Audio (mp3)’, a log entry will be created and it will be allowed to pass through.
B. The file will be detected by rule #2 as a “*.exe”, a log entry will be created and the interface that received the traffic will be brought down.
C. The file will be detected by rule #3 as an Archive(zip), blocked, and a log entry will be created.
D. Nothing, the file will go undetected.
Answer: A
QUESTION 229
What are the requirements for a cluster to maintain TCP connections after device or link failover? (Select all that apply.)
A. Enable session pick-up.
B. Only applies to connections handled by a proxy.
C. Only applies to UDP and ICMP connections.
D. Connections must not be handled by a proxy.
Answer: AD
QUESTION 230
What advantages are there in using a hub-and-spoke IPSec VPN configuration instead of a fully-meshed set of IPSec tunnels? (Select all that apply.)
A. Using a hub and spoke topology is required to achieve full redundancy.
B. Using a hub and spoke topology simplifies configuration because fewer tunnels are required.
C. Using a hub and spoke topology provides stronger encryption.
D. The routing at a spoke is simpler, compared to a meshed node.
Answer: BD
QUESTION 231
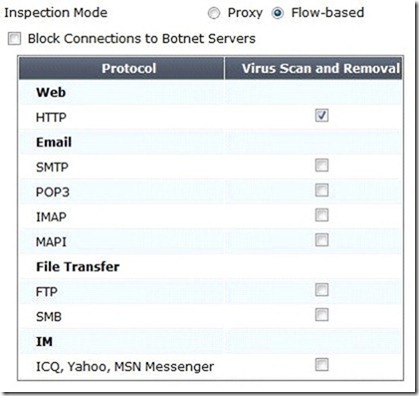
The eicar test virus is put into a zip archive, which is given the password of “Fortinet” in order to open the archive. Review the configuration in the exhibits shown below; then answer the question that follows.
Exhibit A – Antivirus Profile:
Exhibit B – Non-default UTM Proxy Options Profile:
Exhibit C – DLP Profile:
Which of one the following profiles could be enabled in order to prevent the file from passing through the FortiGate device over HTTP on the standard port for that protocol?
A. Only Exhibit A
B. Only Exhibit B
C. Only Exhibit C with default UTM Proxy settings.
D. All of the Exhibits (A, B and C)
E. Only Exhibit C with non-default UTM Proxy settings (Exhibit B).
Answer: C
QUESTION 232
With FSSO, a domain user could authenticate either against the domain controller running the Collector Agent and Domain Controller Agent, or a domain controller running only the Domain Controller Agent.
If you attempt to authenticate with the Secondary Domain Controller running only the Domain Controller Agent, which of the following statements are correct? (Select all that apply.)
A. The login event is sent to the Collector Agent.
B. The FortiGate unit receives the user information from the Domain Controller Agent of the Secondary Controller.
C. The Collector Agent performs the DNS lookup for the authenticated client’s IP address.
D. The user cannot be authenticated with the FortiGate device in this manner because each Domain Controller Agent requires a dedicated Collector Agent.
Answer: AC
QUESTION 233
In Transparent Mode, forward-domain is an attribute of ______________.
A. an interface
B. a firewall policy
C. a static route
D. a virtual domain
Answer: A
QUESTION 234
Review the CLI configuration below for an IPS sensor and identify the correct statements regarding this configuration from the choices below. (Select all that apply.)
config ips sensor
edit “LINUX_SERVER”
set comment ”
set replacemsg-group ”
set log enable
config entries
edit 1
set action default
set application all
set location server
set log enable
set log-packet enable
set os Linux
set protocol all
set quarantine none
set severity all
set status default
next
end
next
end
A. The sensor will log all server attacks for all operating systems.
B. The sensor will include a PCAP file with a trace of the matching packets in the log message of any matched signature.
C. The sensor will match all traffic from the address object `LINUX_SERVER’.
D. The sensor will reset all connections that match these signatures.
E. The sensor only filters which IPS signatures to apply to the selected firewall policy.
Answer: BE
QUESTION 235
In which of the following report templates would you configure the charts to be included in the report?
A. Layout Template
B. Data Filter Template
C. Output Template
D. Schedule Template
Answer: A
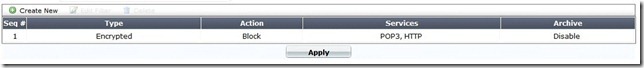
QUESTION 236
A DLP rule with an action of Exempt has been matched against traffic passing through the FortiGate unit. Which of the following statements is correct regarding how this transaction will be handled by the FortiGate unit?
A. Any other matched DLP rules will be ignored with the exception of Archiving.
B. Future files whose characteristics match this file will bypass DLP scanning.
C. The traffic matching the DLP rule will bypass antivirus scanning.
D. The client IP address will be added to a white list.
Answer: A
QUESTION 237
An administrator is examining the attack logs and notices the following entry:
type=ips subtype=signature pri=alert vd=root serial=1995 attack_id=103022611 src=69.45.64.22 dst=192.168.1.100 src_port=80 dst_port=4887 src_int=wlan dst_int=internal status=detectedproto=6 service=4887/tcp user=N/A group=N/A msg=web_client: IE.IFRAME.BufferOverflow.B
Based on the information displayed in this entry, which of the following statements are correct? (Select all that apply.)
A. This is an HTTP server attack.
B. The attack was detected and blocked by the FortiGate unit.
C. The attack was against a FortiGate unit at the 192.168.1.100 IP address.
D. The attack was detected and passed by the FortiGate unit.
Answer: CD
QUESTION 238
What advantages are there in using a hub-and-spoke IPSec VPN configuration instead of a fully-meshed set of IPSec tunnels? (Select all that apply.)
A. Using a hub and spoke topology is required to achieve full redundancy.
B. Using a hub and spoke topology simplifies configuration.
C. Using a hub and spoke topology provides stronger encryption.
D. Using a hub and spoke topology reduces the number of tunnels.
Answer: BD
QUESTION 239
An administrator wishes to generate a report showing Top Traffic by service type. They notice that web traffic overwhelms the pie chart and want to exclude the web traffic from the report.
Which of the following statements best describes how to do this?
A. In the Service field of the Data Filter, type 80/tcp and select the NOT checkbox.
B. Add the following entry to the Generic Field section of the Data Filter: service=”!web”.
C. When editing the chart, uncheck wlog to indicate that Web Filtering data is being excluded when generating the chart.
D. When editing the chart, enter ‘http’ in the Exclude Service field.
Answer: A
QUESTION 240
A network administrator connects his PC to the INTERNAL interface on a FortiGate unit.
The administrator attempts to make an HTTPS connection to the FortiGate unit on the VLAN1 interface at the IP address of 10.0.1.1, but gets no connectivity.
The following troubleshooting commands are executed from the DOS prompt on the PC and from the CLI.
C:\>ping 10.0.1.1
Pinging 10.0.1.1 with 32 bytes of data:
Reply from 10.0.1.1: bytes=32 time=1ms TTL=255
Reply from 10.0.1.1: bytes=32 time<1ms TTL=255
Reply from 10.0.1.1: bytes=32 time<1ms TTL=255
Reply from 10.0.1.1: bytes=32 time<1ms TTL=255
user1 # get system interface
== [ internal ]
name. internal mode. static ip: 10.0.1.254 255.255.255.128 status: up
netbios-forwarD. disable type. physical mtu-override. disable
== [ vlan1 ]
name. vlan1 mode. static ip: 10.0.1.1 255.255.255.128 status: up netb
ios-forward. disable type. vlan mtu-override. disable
user1 # diagnose debug flow trace start 100
user1 # diagnose debug ena
user1 # diagnose debug flow filter daddr 10.0.1.1 10.0.1.1
id=20085 trace_id=274 msg=”vd-root received a packet(proto=6, 10.0.1.130:47927- >10.0.1.1:443) from internal.”
id=20085 trace_id=274 msg=”allocate a new session-00000b1b”
id=20085 trace_id=274 msg=”find SNAT: IP-10.0.1.1, port-43798″
id=20085 trace_id=274 msg=”iprope_in_check() check failed, drop”
Based on the output from these commands, which of the following explanations is a possible cause of the problem?
A. The Fortigate unit has no route back to the PC.
B. The PC has an IP address in the wrong subnet.
C. The PC is using an incorrect default gateway IP address.
D. The FortiGate unit does not have the HTTPS service configured on the VLAN1 interface.
E. There is no firewall policy allowing traffic from INTERNAL-> VLAN1.
Answer: D
QUESTION 241
Which of the following methods does the FortiGate unit use to determine the availability of a web cache using Web Cache Communication Protocol (WCCP)?
A. The FortiGate unit receives periodic “Here I am” messages from the web cache.
B. The FortiGate unit polls all globally-defined web cache servers at a regular intervals.
C. The FortiGate using uses the health check monitor to verify the availability of a web cache server.
D. The web cache sends an “I see you” message which is captured by the FortiGate unit.
Answer: C
QUESTION 242
A FortiGate unit is configured with multiple VDOMs. An administrative account on the device has been assigned a Scope value of VDOM:root.
Which of the following items would an administrator logging in using this account NOT be able to configure?
A. Firewall addresses
B. DHCP servers
C. FortiGuard Distribution Network configuration
D. PPTP VPN configuration
Answer: C
QUESTION 243
Which of the following statements is correct regarding the antivirus scanning function on the FortiGate unit?
A. Antivirus scanning provides end-to-end virus protection for client workstations.
B. Antivirus scanning provides virus protection for the HTTP, Telnet, SMTP, and FTP protocols.
C. Antivirus scanning supports banned word checking.
D. Antivirus scanning supports grayware protection.
Answer: D
QUESTION 244
WAN optimization is configured in Active/Passive mode. When will the remote peer accept an attempt to initiate a tunnel?
A. The attempt will be accepted when the request comes from a known peer and there is a matching WAN optimization passive rule.
B. The attempt will be accepted when there is a matching WAN optimization passive rule.
C. The attempt will be accepted when the request comes from a known peer.
D. The attempt will be accepted when a user on the remote peer accepts the connection request.
Answer: A
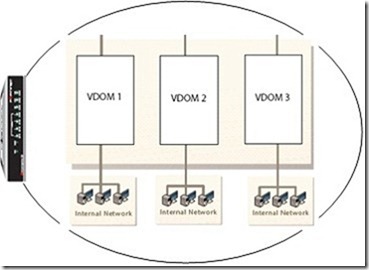
QUESTION 245
A FortiGate unit is configured with three Virtual Domains (VDOMs) as illustrated in the exhibit.
Which of the following statements are correct regarding these VDOMs? (Select all that apply.)
A. The FortiGate unit supports any combination of these VDOMs in NAT/Route and Transparent modes.
B. The FortiGate unit must be a model 1000 or above to support multiple VDOMs.
C. A license had to be purchased and applied to the FortiGate unit before VDOM mode could be enabled.
D. All VDOMs must operate in the same mode.
E. Changing a VDOM operational mode requires a reboot of the FortiGate unit.
F. An admin account can be assigned to one VDOM or it can have access to all three VDOMs.
Answer: AF
QUESTION 246
Both the FortiGate and FortiAnalyzer units can notify administrators when certain alert conditions are met.
Considering this, which of the following statements is NOT correct?
A. On a FortiGate device, the alert condition is based either on the severity level or on the log type, but not on a combination of the two.
B. On a FortiAnalyzer device, the alert condition is based either on the severity level or on the log type, but not on a combination of the two.
C. Only a FortiAnalyzer device can send the alert notification in the form of a syslog message.
D. Both the FortiGate and FortiAnalyzer devices can send alert notifications in the form of an email alert.
Answer: B
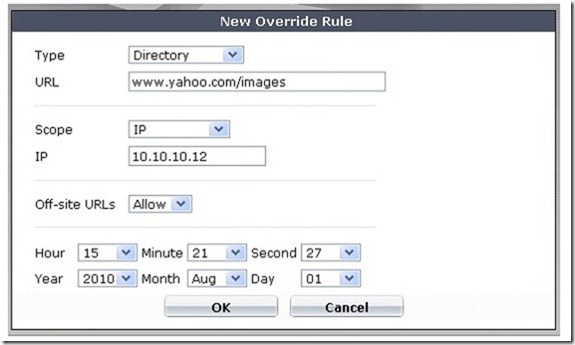
QUESTION 247
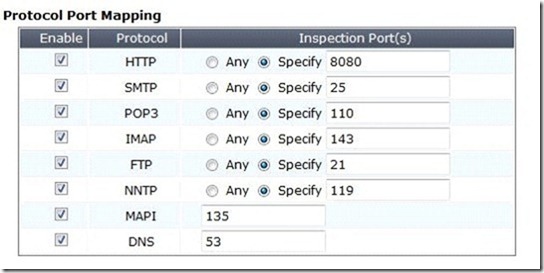
Which of the following statements is correct regarding the FortiGuard Services Web Filtering Override configuration as illustrated in the exhibit?
A. Any client on the same subnet as the authenticated user is allowed to access www.yahoo.com/images/.
B. A client with an IP of address 10.10.10.12 is allowed access to any subdirectory that is part of the www.yahoo.com web site.
C. A client with an IP address of 10.10.10.12 is allowed access to the www.yahoo.com/images/ web site and any of its offsite URLs.
D. A client with an IP address of 10.10.10.12 is allowed access to any URL under the www.yahoo.com web site, including any subdirectory URLs, until August 7, 2009.
E. Any client on the same subnet as the authenticated user is allowed to access www.yahoo.com/images/ until August 7, 2009.
Answer: C
QUESTION 248
SSL Proxy is used to decrypt the SSL-encrypted traffic. After decryption, where is the traffic buffered in preparation for content inspection?
A. The file is buffered by the application proxy.
B. The file is buffered by the SSL proxy.
C. In the upload direction, the file is buffered by the SSL proxy.
In the download direction, the file is buffered by the application proxy.
D. No file buffering is needed since a stream-based scanning approach is used for SSL content inspection.
Answer: A
QUESTION 249
An administrator logs into a FortiGate unit using an account which has been assigned a super_admin profile. Which of the following operations can this administrator perform?
A. They can delete logged-in users who are also assigned the super_admin access profile.
B. They can make changes to the super_admin profile.
C. They can delete the admin account if the default admin user is not logged in.
D. They can view all the system configuration settings but can not make changes.
E. They can access configuration options for only the VDOMs to which they have been assigned.
Answer: C
QUESTION 250
Which of the following statements is correct about how the FortiGate unit verifies username and password during user authentication?
A. If a remote server is included in a user group, it will be checked before local accounts.
B. An administrator can define a local account for which the password must be verified by querying a remote server.
C. If authentication fails with a local password, the FortiGate unit will query the authentication server if the local user is configured with both a local password and an authentication server.
D. The FortiGate unit will only attempt to authenticate against Active Directory if Fortinet Server Authentication Extensions are installed and configured.
Answer: B
More free Lead2pass NSE4 exam new questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDeFZLNEJDeDRQdlE
I purchased the dump one month ago and I learned a lot from the Lead2pass NSE4 practice test. This dump is valid. I just pass the exam with it. The answers are accurate. Recommend.
2017 Fortinet NSE4 (All 533 Q&As) exam dumps (PDF&VCE) from Lead2pass:
https://www.lead2pass.com/nse4.html [100% Exam Pass Guaranteed]